
Accessing the dark web is legal in India as long as you do not engage in illegal activities such as buying drugs or hacking services. Install Tor Browser from the official website, adjust security settings to “Safer” or “Safest,” and only use trusted onion links from verified directories. This blog offers a complete guide on how to access the Dark Web using the Tor Browser, along with step-by-step instructions, security tips, legal warnings, and real-world examples. If you make use of a password manager, then it may come with a feature that monitors the dark web for mentions of your email address and password, or any other personal details.

Encrypted Communication Tools
In some countries, evading government restrictions to seek new political ideologies is punishable. For example, China uses the Great Firewall to block access to Western sites. Accessing blocked content can result in being placed on a watch list or imprisonment.
Best Dark Web Sites: Unseen Onion And Tor Links
Certain details of your traffic can be intercepted at the entry and exit points of the node, by the people running those nodes, if they know what they’re doing and what they’re looking for. You’re also open to threats like end-to-end correlation attacks, so while Tor is a lot more secure and private, it’s by no means completely safe. Now that you understand the essentials of anonymous networks and how to prepare yourself for secure browsing, it’s time to explore the practical steps involved in accessing the Dark Web. While the process is not overly complicated, it demands attention to detail, adherence to best practices, and an understanding of the risks. The Dark Web marketplace sells several products and services. Perhaps the best-known thing you can buy on the Dark Web is information collected in what seems like the almost daily data breaches we read about in the news.
Accessing Onion Sites On Android
Questions, comments and discussions of markets must be posted inside the Market sticky. Ads must be relevant to r/darknet, as well as posted in the correct sticky. Posts which violate this rule will be removed; repeat offenders will be banned. For example, if you’d like to discuss shipping and logistics, please see r/usps, r/ups, r/logistics, etc. If you’d like to discuss things you can buy on the darknet, please see the subreddit related to that specific thing. Connection issues are almost always solved by finding, and then using, a verified link to a mirror.

How Can Beginners Detect And Analyze PDF Malware Step By Step?

As digital landscapes evolve, so do the methods of accessing hidden content and maintaining anonymity. By following these steps, you enter the Dark Web with more confidence and preparedness. Although it’s not inherently illegal to access the Dark Web, remember that certain sites and activities may be. Stay vigilant, trust your instincts, verify sources, and prioritize your security to make the most of the anonymity these networks provide. I2P is an anonymous overlay network designed primarily for peer-to-peer applications. As the most widely used anonymity network, Tor routes your internet traffic through a series of volunteer-run servers (relays) around the world.
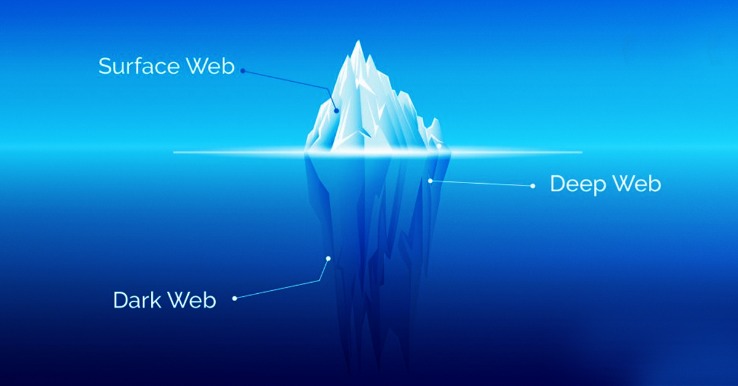
Did you know that Google only shows you a glimpse of all the websites that actually exist? The last time I checked, it’s estimated that the entire web is roughly 500 times larger than what Google returns in Google Search. PCMag.com is a leading authority on technology, delivering lab-based, independent reviews of the latest products and services. Our expert industry analysis and practical solutions help you make better buying decisions and get more from technology.
I’m Looking For Mods For This Sub Note: Not Reading This Numbered List In The Description Means Disqualification
Combined with smart surfing behaviour and technologies like Tor and a VPN, even the darkest reaches of the internet may be securely traversed. Although I am quite scared of being tracked, watched and all the shit that sounds stupid, i’m genuinely curious about exploring the deep web. Not only that but I am scared about my private information being used and sold to companies. I’ve been reading lately on how much about ourselves isn’t actually private. Plus, in our day in age, getting to know computers a bit more ain’t a bad idea in my opinion.
Roundup – Best VPNs For The Dark Web
If you choose to visit the dark web, you must take the necessary measures to protect your privacy and security. If you know the right websites, you can easily access a tremendous amount of information, including research articles, news stories, and more. If you don’t know what you’re doing – and this post is made for people that don’t – then I highly recommend you don’t use a VPN with TOR.
Everything You Need To Know About The First Dark Web Market: The Silk Road Website
The dark web, or dark net, is a small part of the deep web that is kept hidden on purpose. Websites and data on the dark web do typically require a special tool to access. Onion links are URLs that end with .onion and can only be accessed through the Tor network. While not mandatory, using a VPN adds an extra layer of privacy and security by hiding Tor usage from your internet service provider. Accessing the Dark Web using the Tor Browser is not just about exploring hidden parts of the internet—it’s about understanding privacy and cybersecurity in the modern world. Cybersecurity Student → Conducts research on privacy tools → Accesses ethical hacking forums (legal) using Tor.
ExpressVPN is an excellent choice for Tor and accessing the Dark Web. It has a proprietary onion site in the Tor network to give you safe access even if your country restricts VPN usage. The most interesting thing about NordVPN is its built-in Onion over VPN feature.
I thought of maybe creating a python script that automates searching random onion links, but 99% of the time it mightn’t not work. In terms of functionality, I don’t think there are too many differences between regular IMAP, POP3, and SMT services and the stuff you can use to communicate on the dark web. A VPN hides your internet activity, making it harder for your connection requests to be traced back to you. It’s a precaution to protect yourself before diving into the dark web.
- Another website is Dread, which is often called the “Reddit of the Dark Web.” It’s a community platform where users can discuss new markets, share onion links, add reviews, and much more.
- Think of Tor as a regular browser like Firefox, Google, or Safari.
- The only difference is that it passes your traffic through random nodes before reaching the destination.
- It allows you to search for images, maps, files, videos, social media posts, and more.
- The provider also offers a dedicated CyberSec suite that prevents annoying ads and blocks malware and trackers.
- Here, you’ll find links to various resources, including educational archives, private forums, anonymous services, and more.
That means that when Tor is compromised, or perhaps there’s a new vulnerability exploit in the Tor network, a VPN will still protect your privacy. The compromised Tor exploit might trace back to you, but then again, your VPN will lead it somewhere else – which makes it impossible to be traced back to you. It’s not a secret that ISPs (Internet Service Providers) and the FBI are tracking Tor users. Obviously not all Tor users, but you never know whether someone might be looking into you. It’s important to arm yourself with a good VPN (Virtual Private Network) when you want to enter the dark web to protect your privacy and anonymity. So, to get into the Tor network, follow the steps I’ve listed below.
These sites are a hybrid tutorial-underground where wannabe hackers ask questions and professionals sell their services or stolen data. Onion links have no regular domain names registered under the domain name registry. Instead, they are designed using a cryptographic key and can be accessed only through software like the Tor browser. One option is to try DuckDuckGo’s .onion version, which is great for privacy. Other options include Ahmia and NotEvil, which focus on listing .onion links.
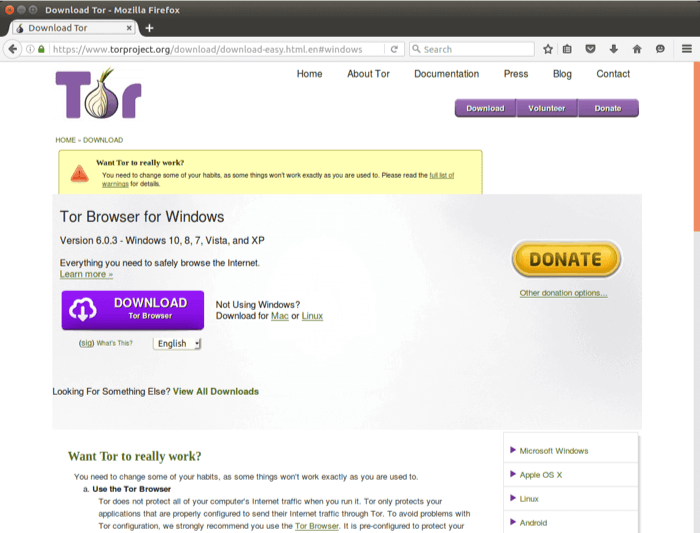
Then, simply click the operating system that you are using and download the file. The site offers downloads for macOS, Windows, Linux, and Android. While an iOS version of the official Tor browser is not available, there are Tor-compatible browsers available in the App Store. So, once you’ve activated your VPN and your privacy is secured, it’s time to visit Tor’s official download page. But again, your ISP won’t be able to see any of the content you’re reading or what you are sending and receiving through the Tor network. As you are now familiar with the three different sections within the entire world wide web, let’s take a closer look at how you can access the dark web anonymously.



