
On the dark web black markets, a teen can buy and sell almost anything—while staying totally anonymous. We’re talking all kinds of illegal drugs (heroin, benzos, Ecstasy, marijuana, to name a few), guns, and child pornographic material. Counterfeit money, stolen credit card information, hacked bank account information, forgeries, stolen artwork. When teens discover forums free from traditional moderation, it feels like they’ve stumbled into the Wild West of the internet. These spaces discuss everything from hacking techniques to political extremism, offering unpolished and often dangerous perspectives.
Types Of Online Sexual Exploitation
The judge in that case, Benoit Gagnon, reportedly wrote in his ruling that there was plenty of harm to children. Two officials from the US Justice Department’s Child Exploitation and Obscenity Section told The Washington Post that AI-generated images depicting “minors engaged in sexually explicit conduct” are illegal under at least two US laws. Fake AI child sex images moving from dark web to social media, researcher says. TikTok told the BBC that, as a result of our investigation, it had now banned sharing links to Omegle.
How Do People Access The Dark Web?
The accuracy is as expected and actually quite consistent with previous research (93.5%) for Tor content classification20. Impreza Hosting’s .onion link provides hosting services designed for Dark Web users, offering anonymous and secure solutions for websites and applications. The platform supports various hosting plans, including shared and VPS hosting, and has served thousands of clients looking for private hosting options. Impreza Hosting also includes features like DDoS protection and cryptocurrency payment support.
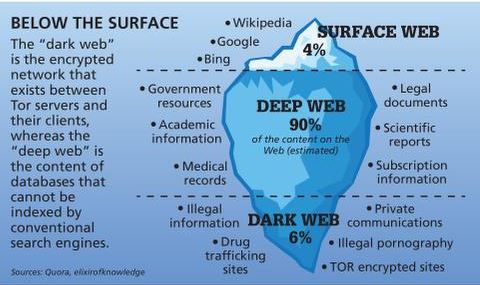
It means you cannot access websites on the dark web with regular browsers like Firefox or Chrome. Instead, you need a specific configuration, software, or authorization, such as Tor, to access it. Its .onion site provides an additional layer of privacy and security for users accessing their Bitcoin wallets or exploring transaction data, especially useful in regions where cryptocurrency sites might be monitored or blocked. Blockchain even has an HTTPS security certificate for even better protection.
Within darknet CSAM forums, articles and videos about the operation were critically analyzed, resulting in an update of security advice from forum administrators. Browsing the dark web can expose users to various risks, including encountering illegal content, malware, scams, and surveillance. Users may also inadvertently break the law by accessing certain illegal websites or participating in illicit activities. When it comes to the dark web and teens, it’s dangerous for teens, so parents should educate their children on internet safety and openly communicate with their teens about their internet usage.

Regular Forum Members
- There are currently a few platforms offering anonymous internet access, including i2p, FreeNet and Tor.
- Open up Tor, and you won’t suddenly see the dark web staring back at you.
- Doing tech-free activities may help your teen to disconnect from their devices and be less invested in the Dark Web.
- The release of Freenet in 2000 is considered by many as the start or founding of the dark web.
- The purpose was to protect U.S. army soldiers and agents in the field, but also politicians who held secret meetings and conversations, which contained the highest security measures.
In the current review article, we summarize both the scientific literature and evidence obtained from CSAM forum “take-downs,” to describe the organization of darknet CSAM forums and the activities of their members. Not all forum members contribute equally to the community, and especially administrators appear indispensable for the proper functioning of the CSAM forum. The CSAM communities continuously monitor the actions and prosecutions that are taken by LEAs, especially when it comes to identifying darknet users. In an operation conducted by Homeland Security Investigations (HSI) in 2012 in the United States—codenamed Operation Sunflower—123 child victims of sexual abuse were identified and rescued. This operation was considered the “first” of its kind, a concentration of LEAs activity on a darknet site. This operation used victim identification specialists, analyzing images seized from child sexual offending websites, including darknet sites.
Make sure they know they can come to you if they need to, regardless of where on the internet it may have occurred. There are many reasons for using Tor, and it does not automatically mean that they are doing anything dangerous or illegal. Lifehacker has been a go-to source of tech help and life advice since 2005. Our mission is to offer reliable tech help and credible, practical, science-based life advice to help you live better. For obvious reasons—I don’t want to get you or me into trouble, after all—I’m not going to get too specific when it comes to what you can find for sale on the dark web.

Power Your Insights With Data You Can Trust
Alicia Kozakiewicz, who was abducted by a man she had met on the internet when she was 13, said the lack of follow-through was disheartening. Now an advocate for laws preventing crimes against children, she had testified in support of the 2008 legislation. “We go home and think, ‘Good grief, the fact that we have to prioritize by age is just really disturbing,’” said Detective Paula Meares, who has investigated child sex crimes for more than 10 years at the Los Angeles Police Department.
Extremist Content And Ideologies
- The highly skilled perpetrators often taunt the authorities with their technical skills, acting boldly because they feel protected by the cover of darkness.
- The US government created the dark web to help its spies communicate and exchange information securely.
- In 2008, the first Tor Browser was released, making it easier for any internet users to access the dark web.
- The phrase matching fails to detect anything that does not describe CSAM with the obvious phrases.
- Escrow has handled thousands of trades, helping to reduce fraud in Dark Web marketplaces.
However, technological advancements such as encryption and privacy-focused browsers like Tor enabled the general public to access it. Some of the deep web sites do not use standard top-level domains (TLD) such as .gov, .com, .net, etc. For instance, services like ProtonMail and SecureDrop (mentioned above already) have hidden sites for their users who live in countries with high levels of censorship.
Quick Links
By better understanding users of CSAM darknet sites, practitioners and LEAs would be better able to address the needs and risks posed by this subgroup of individuals at risk for sexual offences. We hope this review provides researchers and practitioners alike with an overview of the darknet and encourage research to better understand users of darknet CSAM forums, so as to ultimately inform management and prevention efforts. The access to technology and a connected community via the Internet has enabled the distribution, possession, and creation of child sexual abuse material (CSAM) to increase. Although previously seen as an unreliable, slow, and access-restrictive technology, the darknet is now an everyday tool for 2.5 million Internet users (Wise 2022). Home Internet connections and faster upload and download speeds have enabled a technology-driven revolution in the lifestyles of modern society. This is also accurate for individuals who seek to access on-demand CSAM and to communicate with likeminded persons.
Serafini asked Cannon to sentence his client to the minimum 25-year penalty allowed by law. He listed off McIntosh’s various infirmities, which include prostate cancer, high cholesterol, a pulmonary embolism and diabetes — all of which the attorney said almost guaranteed he would die in prison, no matter the sentence. She sentenced McIntosh to 55 years in prison — 15 years fewer than prosecutors recommended, and 30 more than his defense attorney did — and promised to recommend that he undergo psychosexual therapy in prison, “which he is in dire need of.” “He just has one focus in life,” said Assistant U.S. Attorney Gregory Schiller. Julian Assange may have lost much of the goodwill he once enjoyed, but WikiLeaks remains one of the most important sources of uncensored political information. Although you can access its content in any browser, for security reasons the only way to submit documents is through Tor.
Government Monitoring
As for drugs and other merchandise, the darknet not only connects teens with suppliers, but it also allows them to pay for their products with payment networks like Bitcoin. Bitcoin is an open peer-to-peer financial network that uses untraceable digital currency. Although Bitcoins are used on the darknet, they are also legit in purchasing items, like video games. On the darknet, once a transaction has been processed, merchants cleverly conceal, package and ship the product out using everyday shipping services like the US Post Office, UPS or FedEx. To understand the darknet, it’s best to review how the Internet is set up.
Avoid dishonest spying that can lead to a hurtful ambush that will blow your credibility. If you’re straight with them that you will check their online content, they’ll post with better judgment and accountability from the beginning. Ongoing digital conversations not only offer bi-directional teaching opportunities between kids and parents, but it also builds a cooperative relationship and teaches family values. The dark net is a hidden, encrypted overlay Internet network with over 50,000 websites that can only be accessed by the Tor Hidden Services browser.
This demonstrates the need to develop tailored interventions based on the offender’s background and behaviour. During those times, persons attracted to minors congregated in support groups where fantasies were openly discussed among the like-minded attendants. Typically, to avoid the attention of law enforcement, organizers of such support groups ensured no child sexual abuse material (CSAM) was openly exchanged during these meetings. Although illegal, those interested in CSAM could, however, resort to adult book shops selling dedicated magazines, or order periodicals containing sexually explicit images of underaged children by surface mail.



