The dark web is a part of the internet that is not accessible through traditional search engines and requires specific software or configurations to access. The goal was to create a secure and anonymous communication system for government agencies. Mail providers Mailbox.org and Protonmail can also be accessed via an .onion link.
Many dark internet users favor Tor which uses a network architecture originally developed by the U.S. Naval Research Lab as a system of decentralized, anonymous nodes to enable anonymous online communication. Unlike the publicly accessible surface web, the deep web includes sites requiring login credentials but is still accessible via traditional browsers. The dark web is a small, hidden subset of the deep web that requires special tools to access. When you install a VPN, all of your activities on the dark web will be hidden from unwanted snoops from your ISP or the FBI. The VPN is a second layer of extra protection, on top of the protection that the Tor network already offers.

The dark web often intrigues curious users and cybersecurity enthusiasts alike, offering a hidden side of the internet that’s not accessible via traditional search engines. While some see it as a digital underworld, the dark web also hosts various legitimate services. Dark web is usually used for illegal activities so you can’t only rely on the Tor browser and need a VPN for robust privacy and security. A dark web VPN encrypts all internet traffic passing through and from your device and route it via a server of your choice. Because VPN prioritizes privacy while Tor prioritizes anonymity, combining the two adds an extra layer of online security and privacy.
Step 3: Launch Hyphanet
- You can enter .onion URLs directly into the Tor Browser’s address bar or visit directories like The Hidden Wiki to find popular sites on the dark web.
- The difference between the surface web and the deep web is that pages, websites, and content on the deep web are only accessible to authorized users with the appropriate credentials.
- So, you should be aware of your actions and adhere to local laws to avoid engaging in illegal activities.
- You can check out this guide on the best antivirus software applications today.
- Files on the dark web can contain malware, ransomware, or other harmful software.
The dark web has no shortage of criminal activity, scams, phishing sites, suspicious links, and malware designed to trick newbies. Links posted to the clear web, in particular, are often malicious. And because there’s very little use of HTTPS on the dark net, verifying whether or not a website is genuine using an SSL certificate is not feasible. Tor is a network of volunteer relays through which the user’s internet connection is routed. The connection is encrypted, and all the traffic bounces between relays worldwide, making the user anonymous. In this guide, we’ll cover the dark web access guide, explain how to use Tor browser safely, and answer key questions like is it safe to browse the dark web.
Is The Dark Web 99% Of The Internet?
Avoid logging into accounts that are linked to your real identity. Instead, use disposable email services and end-to-end encrypted communication tools like ProtonMail or Signal. If you need a way to organize as an activist or you want to discuss censored topics with others, my first suggestion is to stick to offline meetups. The second, less secure option is to use encrypted messaging apps with ties to specific non-profit or activist organizations. For example, Briar is an extremely private chat app designed to help journalists communicate anonymously with sources.
Dark Web Chat/Social Networks
While it’s generally safe to use, dark web activity can be detected at the entry and exit nodes of the Tor network. TOR (The Onion Router) is a software that makes it possible for users to communicate and browse the internet anonymously. This is achieved by directing internet traffic through a global network of servers, which conceals the user’s identity and location. The main purpose of TOR is to provide access to the dark web and bypass censorship and surveillance in countries with restricted internet access. On the other hand, the TOR browser is a web browser that uses the TOR network to offer users private and anonymous internet browsing.
Purchase Legal Goods Secretly

Lastly, the dark web is the portion of the deep web that is generally inaccessible and is much larger than the surface web. It relies on P2P connections and requires specialized tools and software. Tor and I2P are the two commonly used tools for accessing the dark web to provide anonymity. It is easily accessible by the general public and requires no special configuration. You can find sites like Facebook, Wikipedia, e-commerce sites, YouTube, and more here. The dark web is part of the internet that is not indexed by standard search engines like Google, Yahoo, and Bing.
David is a programmer and writer who has worked as a software developer at MIT. He holds a BA in history from Yale and is currently pursuing graduate studies in computer science at UT Austin. His writing typically combines his expertise in software, technology, business, and finance. A reliable, fast, and user-friendly VPN service offering lots of customizable options for privacy geeks.

Ways Small To Midsize Businesses Can Stay Safe In The Cloud
The content of all these pages is stored on Google’s servers, but it’s mostly outdated, old content; smartphone app content; journals; court records; private social media profiles, and much more. By following these steps, you’ll have I2P and Hyphanet set up for secure and private browsing on the dark web. Both networks have unique strengths, and while they aren’t as user-friendly as Tor, they offer excellent alternatives for those seeking robust privacy and decentralized communication options. I2P (Invisible Internet Project) is an open-source network designed to allow anonymous and private communication. Although it’s not as widely used as Tor, I2P can provide robust anonymity and is well-suited for peer-to-peer file sharing.
Connect To A VPN Before Opening Tor
While there is a lot of criminal activity on the dark web, there’s nothing actually illegal about accessing the dark web. In certain countries, the dark web facilitates political discourse and conversation that would otherwise be censored, outlawed, or eradicated in entirety. ExpressVPN protects your internet traffic using 256-bit AES channel strong encryption together with 4096-bit DHE-RSA keys and a SHA512 hash authentication. The company has an independently audited no-logs policy and its comprehensive server network is RAM-only. It comes with DNS leak protection and works well if you’re aiming to improve online privacy. While connected through NordVPN, your internet traffic is protected using AES 256-bit encryption.
How To Browse The Dark Web Legally
Our expert industry analysis and practical solutions help you make better buying decisions and get more from technology. I don’t recommend seeking out dark web content unless you have a specific reason to do so. If you want to observe the lawless sides of the internet from afar, check out YouTube videos of dark web explorations, like this one from John Hammond, to satisfy your curiosity. Copy your desired onion URL and paste it into the address bar at the top of the screen to begin searching on the dark web. Alternatively, if the website has turned the onion URL into a link, you can click on that in the Tor browser, and it will automatically open the dark website. When the Tor Browser is launched, you will be brought to a purple homepage with a search field for the DuckDuckGo search engine in the center of the screen.
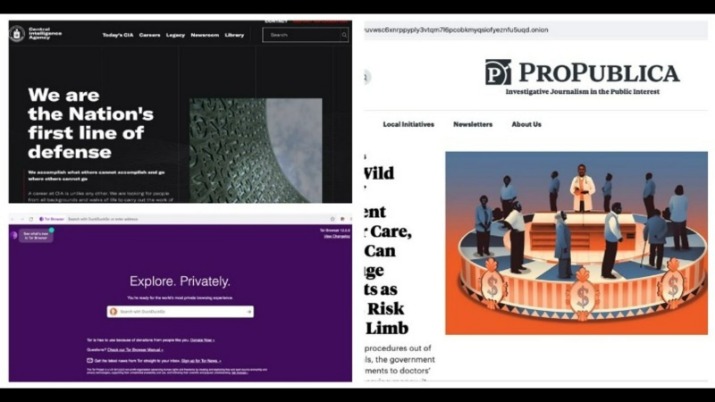
Indeed, Facebook, The New York Times and now even the CIA have sites on the dark web, hosting “onion” versions of their pages that can be accessed via the Tor browser. The spy agency is hoping to securely and anonymously collect tips, though its entire website, including job listings, are available on the onion service. Hendrik is a writer at vpnMentor, specializing in VPN comparisons and user guides. Hackers on the dark web can easily access your personal data using trojans, phishing, and other types of fraudulent websites or programs.
- The platform is protected from government interference and malicious attacks to protect the user.
- Many countries, such as Qatar, China, Cuba, Russia, and Turkey, censor internet content promoting political dissent.
- A Dark Web alert is a notification service that informs you if your personal information has been found on the Dark Web (for example, email addresses, passwords, or credit card numbers).
- The provider also offers a dedicated CyberSec suite that prevents annoying ads and blocks malware and trackers.
I also recommend that you browse the dark web with complete anonymity by using a VPN — just to be safe. It routes all traffic through Tor, preventing IP leaks and offering stronger protection against tracking. Alternatively, Linux distributions like Qubes OS provide advanced security features for those needing long-term privacy-focused computing. IP2 is faster than Tor and offers stronger peer-to-peer security, as it uses one-way tunnels to encrypt traffic — meaning, only inbound or outbound traffic could be intercepted, not both. In addition, it uses a distributed network database which is harder to attack than Tor’s fixed, trusted Directory servers.



