While this market started in Canada in 2021, WeTheNorth now sells to both Canadian and international users. It’s a market for fake documents, hacking software, and financial fraud services. WeTheNorth has a strong community vibe, with an active forum where users interact and share updates. The dark web itself is not illegal, but it’s largely connected with unscrupulous and illegal operations. It is used by many for buying or selling items that are prohibited on the regular internet, like fake IDs, illegal drugs, and stolen data.
Stay Within Legal Boundaries

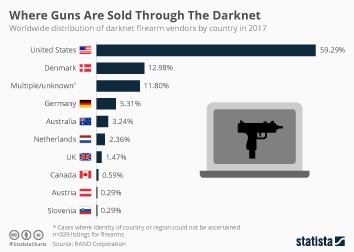
The marketplace requires merchants to pay fees to sell their products, helping ensure a certain level of quality control. One of the biggest problems cybersecurity teams face isn’t a lack of tools — it’s too many alerts. This chart shows the worldwide distribution of darknet firearm vendors by country in 2017. Having JavaScript enabled on the dark web can cause havoc because it can reveal your IP address to your website. Also, previously, the Tor browser was vulnerable to JavaScript attacks as it provided hackers a pathway to track your activities by using the session details. Therefore, for security reasons, disable JavaScript on the Tor browser and enjoy an anonymous browsing experience on the dark net.
It aims to preserve the internet’s scientific and cultural heritage. Using the ProtonMail .onion site offers security and privacy advantages. Moreover, the company also uses HTTPS and SSL encryption on the Onion site for extra protection. This makes it even harder for third parties to see your email traffic. This service is a good source of statistics if you have a school project requiring research on Tor and the dark web. However, note that the site only uses non-sensitive and public data for the metrics.

Simple mistakes—such as inadequate operational security practices, sharing identifiable details, or using compromised devices—can quickly compromise anonymity and expose users’ real-world identities. Finally, product variety significantly influences marketplace choice. Marketplaces that maintain strict moderation policies—banning excessively harmful or exploitative products—also gain popularity among more ethically minded users. Known for its publicity stunt releasing millions of stolen card details for free, BidenCash specializes in credit card fraud and identity theft. These features help establish trust between buyers and sellers, providing users with a sense of security that many other markets lack.

Criteria For Choosing The Best Dark-Web Marketplaces
- Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with the use of this material.
- Transactions are conducted through Bitcoin and Monero which provides anonymity for both buyers and sellers.
- The buyers, or “consumers,” are cybercriminals who use these tools to launch illegal activities.
- Once received by the buyer, the compound could be pressed into counterfeit pills, like M30s, and further distributed to end consumers.
My film explains the darknet gun market truth of our still broken financial system, and how our pensions and our savings are still very much at risk. The good thing about using this website is that you do not have to purchase any products or services on the site to get started. The market facilitates trades in stolen credit card data, hacked bank accounts, and services to facilitate the laundering of cryptocurrency.
What We Know So Far About The Supposed ‘Mother Of All Data Breaches’
However, you should not see it as an opportunity to engage in illegal activities to avoid trouble with authorities. While Tor offers anonymity on the dark web, your online activities leave breadcrumbs that can reveal your identity. That is why you should only use a reliable VPN like ExpressVPN or NordVPN for additional security and privacy.
- “The sellers were very clear about how the transaction would go, which underscored the need for consistent secrecy,” says Holt.
- As a user or cybersecurity professional, approaching these marketplaces demands utmost caution, thorough knowledge of operational security, and constant awareness of legal boundaries.
- The browser uses onion routing technology to route the internet traffic through multiple relay nodes that provide layered encryption.
- It is common for darknet vendors to talk about their delivery and stealth methods to reassure customers that their purchases will be delivered as advertised and not seized by the authorities.
Exploring The Onion Dark Web: A Comprehensive Guide
It allows access to the .onion sites on the dark web that you won’t find using a regular browser. Some fake sellers take your crypto and never ship what you ordered, or phishing sites that look like real marketplaces but steal your login info. And then there’s malware—click the wrong link or download the wrong file, and your device could get infected. By supplying stolen data, these dark web links fuel many online scams and identity theft operations, playing a critical role in the darker aspects of the internet. While all six face charges for racketeering, money laundering and extortion, Vassell also faces charges for grand theft. Investigators said those items were then sold to pawn shops around Orlando.
Marketplaces And Platforms
The biggest and most frustrating part about dark websites is that they live for a short span of time. These platforms keep changing their addresses to avoid DDoS attacks or law enforcement agencies. Blockchain even has an HTTPS security certificate for even better protection. Hence, if you participate in them, whether knowingly or unknowingly, you can end up putting criminal charges on yourself, and in some extreme cases, even imprisonment. Overall, dark-web marketplaces inherently involve substantial risk, and users must thoroughly understand these threats.
Illicit And Risky Use-Cases
Check out these best onion sites to access the dark web securely and anonymously. By consistently applying these straightforward security tips, you can significantly mitigate risks and better protect your privacy, finances, and legal standing when interacting with dark-web marketplaces. It allows vendors to sell without registration, which provides an added layer of anonymity, making it one of the more flexible and user-friendly markets on the dark web.
Throughout 2024, DNM vendors also sent far more value to personal wallets and stored funds on-chain. In some ways, the dark web offers more browsing freedom, but the lack of safeguards can leave you exposed to hackers, malware, and other online threats. Before you access deep web sites, you need to be aware of the dangers that can lurk on the dark web, such as viruses or other malware. Tor Links is a backup directory of “.onion” sites in case other directories go offline. It hosted over 7,000 .onion categorized links to make surfing the web easier. One of Daniel’s impressive features was the built-in functionality that showed whether a particular dark website is online.
Accessing Onion Sites On Android
Guns are sold on the dark web through online marketplaces, similar to legal e-commerce sites. On one hand, it offers privacy for whistleblowers, journalists, and citizens in oppressive countries. On the other hand, it’s notorious for enabling illegal activity, including drug sales, weapons trafficking, counterfeit ID trading, hacking services, and the exchange of stolen personal data. Despite Telegram’s anonymity, the dark web is still a hot spot for illegal trading of malware, illicit goods, and stolen data (such as stolen credit card information).
Anyone considering engaging with these platforms must carefully evaluate potential consequences, exercise stringent security practices, and remain vigilant to minimize exposure to these significant hazards. Ideal marketplaces support anonymous browsing through networks like Tor and I2P, utilize privacy-focused cryptocurrencies such as Monero, and implement measures to prevent tracking and transaction tracing. Platforms that provide clear guidelines for maintaining operational security (OpSec) and offer built-in tools for data obfuscation are especially favored. This marketplace focuses on selling stolen financial data, such as BINs (Bank Identification Numbers), RDP/VDS access, and verified crypto accounts for money laundering. Another dark net marketplace that has grabbed a lot of attention is the Hydra market.
Supposedly, these weapons were somehow put aside from the received supplies and are now being made available to terrorists looking to buy rocket launchers and other high-impact attack systems. “The sellers were very clear about how the transaction would go, which underscored the need for consistent secrecy,” says Holt. “What it does is it causes the firearm to fire in rapid succession in a full auto-mode.,” Ector explained.
Explicit And Illegal Content
Launched after the takedown of AlphaBay in 2021, Abacus Market has rapidly risen to prominence. It features over 40,000 listings including narcotics, counterfeit items, hacking tools, and stolen data. The marketplace is well-known for its bug bounty programs and robust security mechanisms, including mandatory 2FA. To prevent the users from DDoS attacks, it provides personal marketplace domains to high-volume buyers and sellers. Moreover, this shop provides detailed statistics about each user profile on the platform, giving users a better idea about the vendors for the buyers and vice versa.
Shifts In User Behavior And Marketplace Structures
Furthermore, data will help to detect attacks against the network and possible censorship events. In some countries, such as China and North Korea, the government uses heavy online censorship and blocks many dark web websites. This is where an Onion website, like the Tor browser, comes in handy.



