
Malware is a type of malicious software that can spy on you, log your keystrokes and steal your personal information. As mentioned above, some common use cases for the deep web include accessing paid subscriptions and online accounts. However, since the dark web has to be accessed intentionally using the Tor browser and a VPN, most people won’t access the dark web in their day-to-day lives.
Security Risks
- Hence, there are massive differences between Dark Web and Deep Web.
- The commercialization of cyber threats continues to accelerate, with at least four major RaaS services advertised in underground forums, including Medusa, Wing, BEAST, and Cicada 3301.
- It’s vast and houses everything from your email to data protected behind paywalls.
- There’s a lot of confusion out there about how to distinguish between these two terms, which both define hidden aspects of the Internet.
- Neither would a password that you’ve typed online and that a website needs to remember to provide you access.
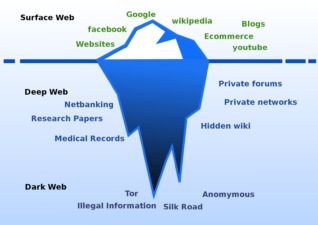
They’re able to access books or academic journals that may not be available on the surface of the web and make payments using ostensibly anonymous currency like Bitcoin. Another category of dark web users includes journalists and whistleblowers who want to share confidential or sensitive information without fear of censorship or legal action. The Deep Web encompasses all online content that standard search engines like Google, Bing, or Yahoo cannot index. These hidden areas of the internet typically require some form of authentication or specialized access to view, making them invisible to general web crawlers. Contrary to popular belief, the Deep Web doesn’t solely exist for illicit purposes—in fact, a large portion of it is entirely legal and critical for day-to-day operations in the digital world.
However, the difference between the two is that it is hidden on purpose and cannot be accessed using standard browsers. United States Military researchers designed the technological infrastructure used to forge the dark web in the 1990s to allow intelligence networks and spies to communicate clandestinely. Also referred to as TOR, or The Onion Router, it utilizes encryption, an application layer inside a protocol communication stack akin to onion layers, hence the name. Since the United States Military constructed it, why would they make the dark web accessible to anyone using the proper tools? The goal was to make Tor available for public domain use eventually. The logic was that messages couldn’t be hidden if nothing was available for them to hide behind.
Legal Implications
Due to limited accessibility, we are generally unaware of the relative scale of the deepweb and darkweb in comparison to the surface web. To understand the difference further, let us go over the basics of how internet search engines work. Search engines use a concept called “indexing” to organize information before a search. This enables the fetching of responses to queries sent by you and me.
- As with most things in life, in this debate, too, there are enough shades of gray; some just happen to be darker than others.
- Unlike the dark web, which is deliberately obscured by layers of technology, the deep web exists just below the surface web.
- The vast portion of the internet not indexed by search engines, including private databases and password-protected sites, which are primarily used for legitimate, secure data storage.
- It is also advisable for users to look for phishing scams, where criminals share communications that seemingly originate from a reputable source.
- On the Deep Web, these risks primarily relate to the fact that you need to authenticate to access a private site and that these sites contain a great deal of sensitive and valuable personal data.
- Other important censored services—such as human rights organizations, VPN services, and advocacy groups—provide a darknet mirror of their websites.
Founded in 2011 and shut down by the FBI in 2013, the Silk Road was a black market for all kinds of illegal activity. Due to encryption and other privacy features, catching criminals on the dark web is difficult, and often requires agencies such as the FBI going into deep cover to try and surface criminal activity. Hence, the deep web literally comprises all those parts of the internet that are not indexed by search engines. The kinds of content present in this region include private databases, medical records, academic journals, and other sensitive information that requires special permission to access.
Is The Deep Web Or Dark Web Safe To Access?

Below, we’ve included an explanation of the deep and dark web and their differences. Security teams often focus on dark web monitoring while overlooking equally critical deep web sources like GitHub or Telegram. However, threats can often originate in the deep web before escalating to the dark web. The dark web is the traditional place for threat actors to engage in cybercrime through selling stolen credentials, sharing guides for techniques, posting ransomware victims’ information, and more. While Tor protects you and gives you anonymity on the dark web, we recommend that you don’t use the dark web. If you still wish to access it, don’t use your regular email and ensure your Tor applications are updated.
Educate Yourself On Emerging Threats
Therefore, this content is inaccessible to most online users, and it is difficult to track the visitors of such websites. Apart from this, Tor allows users to access URLs ending with .onion through its ‘hidden services’ functionality. Users need this browser to access this special category of websites.
In combination with the rise of cryptocurrencies, the dark web has enabled billions of dollars in illegal trade. The “deep” web then, is all of the stuff connected to the internet but hidden away behind some form of security. Reports suggest that the deep web comprises about 90% to 95% of the entire internet while the dark web accounts for 0.01% to 5% of it. However, it’s wise to be cautious while accessing the content from suspicious sources to avoid illegitimate content. One we’ve encountered is a scammer pretending to be the admin of an exclusive forum we tried to sign up for. They asked for our personal information in exchange for access to the forum.
Enable MFA On Your Accounts
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. See what external threats are exposed for your organization by signing up for our free trial. It is important to practice internet safety and security—and that rings true even if you use the Surface Web.
Most People Access The Deep Web Everyday, But Not The Dark Web
Of course, we know this isn’t true, and the surface web only comprises just a small percentage of the entire internet. Most of the internet is divided up into restricted pockets known as the deep web. On the other hand, the deep web is that hidden part of the internet, which is personal and open to its respective owners. For instance, Harvard University received a bomb threat via a disposable email in December 2013. They immediately informed the FBI, which singled out all the campus students using Tor in that time frame.
On the other hand, the dark web takes privacy to a different level, allowing users to browse and communicate completely anonymously. When most people think of the dark web, they often think of illegal activity. Though the level of anonymity on the dark web has made it a haven for criminal dealings, that’s not all it’s used for. It’s also used by regular people looking to browse privately and ensure their information or internet traffic isn’t monitored or tracked.
The deep web vs dark web are often misconstrued as being one thing when in reality they represent two different levels of the internet. The deep web refers to all that is accessible on the internet that is not indexed with those typical search engines. This would include a very broad range of content such as private databases, academic resources, and password-protected sites. Unlike the surface web, which is easily accessible and often serves legitimate purposes, the deep web holds valuable information that typically requires specific access credentials or subscriptions. Deep web, a part of the Internet that extends beyond the reach of search engines such as Google, Yahoo! The term “deep web” was coined in 2001 by computer scientist Michael K. Bergman, who differentiated it from the “surface web,” where openly viewable and retrievable content resides.
For comprehensive protection against scammers, viruses, and ransomware across every layer of the internet, get Norton 360 Deluxe. Despite its reputation, many people use the dark web for legitimate purposes, such as secure communication for journalists, activists, and those seeking uncensored information. Accessing the deep web is simple, and you likely use it daily when logging into private accounts like Gmail, your bank account, or even streaming services like Netflix or Disney+.
Legal Vs Illegal Activities
The goal of TOR was to allow secure communication by intelligence sources in dangerous environments and has since been adopted by the general public for secure, anonymous browsing. The scale and impact of the Dark Web expanded with the development of cryptocurrencies like Bitcoin, which allow semi-anonymous financial transactions to be performed on the Internet. Though deep web content and services are largely safe and legal, the risk of your login credentials falling into the wrong hands is real. Remember that nearly all the websites you access on the deep web require password authentication. A small, hidden part of the internet accessed via special tools like Tor, often linked to anonymity and sometimes illegal activities, but also used for legitimate purposes like secure communication.
Another factor to note is that while your traffic is encrypted several times, it’s not encrypted as it exits the last server in the chain. Law enforcement officials in some countries have been found to run or seize exit nodes to monitor dark web traffic. If your traffic passes through a compromised node, the authorities can see your real IP address and potentially trace the activity back to you. Accessing the dark web is legal, but what you do on the dark streets matters. If you engage in any criminal activity and you’re caught in the act, you could face the full force of the law. Cloudwards.net may earn a small commission from some purchases made through our site.



