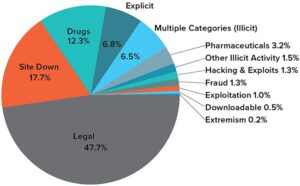
Other business segments like retail or pharma are more susceptible to nontraditional attacks like brand spoofing in the form of fake domains or phishing attacks, according to Schneider. In his view digital footprint monitoring is a particularly valuable tool and will often include a dark web component. Further, takedown services are a natural step beyond digital footprint monitoring. In general, individual businesses won’t have the required contacts with internet services providers, cloud hosting platforms, and even law enforcement, to effect takedowns on their own. Every organization must strengthen its cybersecurity posture, and investment in dark web monitoring has become a must for the protection of sensitive information and to ensure the continuity of business operations.
NCSC Assured Cyber Incident Planning & Response Course

When a threat is discovered, users can create a customized alert that notifies team members and anyone else in the organization who is relevant to the threat, such as marketing, legal, human resources or fraud teams. Security teams widely use the tool to enhance their threat intelligence capabilities and improve cybersecurity resilience. It scans the dark web for compromised data, including personal information, credentials, and intellectual property. Its comprehensive platform includes threat intelligence feeds, risk analysis, and incident response support. DarkOwl’s advanced analytics and machine learning capabilities help detect and prioritize threats, enabling proactive security measures.
Is My Data Transferred To Third Party Services For Scanning?
When hackers break into company databases, they strip away as much user information as possible and sell it on the Dark Web. This can include personally identifiable information (PII), like your Social Security Number (SSN) and passwords, email addresses, or even intellectual property. Most people don’t know how to access the Dark Web safely and will never know if their passwords or identity are at risk. In that case, you should immediately change compromised passwords, notify parties that may have been affected, enable multi-factor authentication, and consult with cybersecurity professionals. Depending on the severity of your breach, you may contact the legal authorities as well to seek legal aid. The tool’s user-friendly interface and customizable alerts enable security teams to stay ahead of cybercriminals.
Google Makes Dark Web Monitoring Free For Everyone
- As technology continues to evolve, so do the methods and techniques used by cybercriminals to exploit the anonymity of the dark web.
- Dark web monitoring tools are indispensable in identifying threats early, detecting breaches, and safeguarding sensitive data.
- Keep an eye out for any suspicious behavior and any security breaches to make sure your company’s data is protected.
- A network fabric is a mesh of connections between network devices such as access points, switches, a…
Instead, Dark Web monitoring works best as an early warning system – which allows you to take defensive action before their compromised data is widely exploited. Dark web monitoring tools work by continuously scanning the dark web for any data that may be relevant to a business. This includes data such as employee credentials, credit card numbers, and other sensitive information that may be stolen and sold on the dark web. Adding dark web monitoring to your overall security strategy enhances your cybersecurity posture. It complements other security measures like endpoint protection and encryption by providing insights into the hidden corners of the web where traditional tools may not reach.

Dark Web Awareness And Cybersecurity Training
The increase in remote work has introduced new security vulnerabilities, as people access sensitive information from various locations, often on personal or less secure networks. Dark web monitoring can quickly identify any exposed data, enhancing the security of remote work environments. Our dark web monitoring technology collects data from the most extensive base of sources in the industry.

Organizations can find out who are behind these data leaks or selling insider information for nefarious purposes by using various dark web monitoring tools. Dark web monitoring reveals loopholes and vulnerabilities that you can’t easily spot on the clear net. You can trace back adversaries’ activities and conduct root cause analysis of major and minor threats.
Our Free Dark Web Monitoring Tool Checks Your Digital Footprint On The Dark Web And More
Reputable providers follow strict privacy and security standards, ensuring your sensitive information stays protected. Dark Web Monitoring helps you stay informed and secure your assets before they’re exploited. Dark Web Monitoring helps protect your personal and business data by alerting you when sensitive information appears on the dark web. By protecting their customer data, businesses improve their reputation and avoid non-compliance penalties. Overall, Dark Web Monitoring acts as an early warning system against cyber attacks, helping you prevent attacks before they happen. Get instant visibility into emerging threats through our dark web monitoring tool, powered by our automated data collection, analysis, and alerting.
The 7 Best Dark Web Monitoring Services In 2024
- Identity Guard uses your email address to scan the dark web for any compromised data.
- This guide provides a comprehensive overview of top dark web monitoring tools, including how to select the right one for your needs and a detailed breakdown of each product.
- That’s why dark web monitoring tools have become an essential part of cybersecurity in 2025.
- Like CrowdStrike, this system requires you to set up a list of identifiers for your company, which include domain names, addresses, and product names.
- When selecting a solution for collecting and analyzing dark web intelligence, look for the following features.
ZeroFox analyzes text images and videos and remediates threats faster by employing the industry’s advanced AI-powered engine. It enables Digital Risk Protection and easily integrates into SIEM, SOAR, TIP, Business Intelligence, and other technologies. Your card will be charged either a monthly or annual fee, depending on the membership plan you choose. If your SSN was found on the Dark Web, scammers could use it to steal your identity, money, and more. The best way to protect yourself and your family from hackers on the Dark Web is to limit their access to your private information. Our browser extension blocks ads, malicious content, trackers, and scams— delivering a faster, safer and cleaner browsing experience and protecting your privacy.
This tool offers advanced search capabilities, enabling users to track specific keywords, phrases, or patterns indicative of cyber threats, illicit activities, or sensitive data leaks. Breachsense supports automated alerts via multiple channels whenever sensitive data is exposed and integrates seamlessly with existing security SIEM and SOC solutions. Breachsense is particularly useful for offensive security teams, mid-market to large enterprises, and government organizations.
Dark Web Monitoring

If you don’t feel safer after signing up for Aura, we offer a 60-day money-back guarantee on all annual plans — no questions asked. 📌 Document all steps taken in response to the alert—this information may be vital for compliance reporting or cyber insurance claims if an actual breach occurred. 💡The FBI Internet Crime Complaint Center (IC3) reported over $10.3 billion in losses from cybercrime in 2023, with business email compromise and credential theft among the leading attack vectors. Yes, many tools alert you when fake domains or phishing campaigns use your brand.
Exploring The Intricacies Of Dark Web Sites
Dark web monitoring solutions help companies detect and respond to such leaks promptly, protecting their competitive position and long-term viability. The dark web can be an invaluable source of intelligence for analysts seeking to better understand the threats against their organization. These are sites where users can upload large amounts of text, including compromised credentials, code, malware and data exposed during data breaches. Most commercial platforms and specialized tools provide access to dark web monitoring services through a user interface or API. Specialized tools and services scan thousands of hidden sites for traces of your data. If something suspicious is found like your bank details or a login you use, you get notified.

Finance, healthcare, retail, law enforcement, government, and education use these tools widely. There are many excellent free NIDS available and you could also consider a SIEM system as an alternative to the DigitalStakeout system. Falcon Intelligence is a subscription service and part of the CrowdStrike family of products that are offered from their Falcon SaaS platform. You don’t have to download and install any software in order to use the Falcon Intelligence service. You don’t have to go through a search engine to get to a website because you can just enter its address in the address bar of your browser or click on a link on another page. However, the test of whether or not a website has been discovered by at least one search engine and indexed by it is the defining characteristic of the bona fide web that we all know about.
For any organization looking for a solution that searches and monitors the dark web across various sources, then DarkOwl is the best option. It offers a complete package that users always look for and thus emerges in the best dark web monitoring tools list. These tools classify the security risks and provide visibility into threats that traditional security tools fail to discover. When the tool detects a threat, it creates alerts and notifies the team members and everyone else within the organization so they can take action to minimize the risk.
Its primary objective is to collect and present sources that are instrumental in enhancing cybersecurity and threat intelligence efforts. Dark Web Monitoring provides a dynamic approach to fraud and identity protection by actively seeking out compromised information, helping you stay one step ahead of hackers and cybercrooks. GBHackers on Security is a top cybersecurity news platform, delivering up-to-date coverage on breaches, emerging threats, malware, vulnerabilities, and global cyber incidents. CIH is an ideal tool for Managed Security Service Providers (MSSPs) and businesses that need to efficiently monitor for credential leaks and other dark web threats.