Get the latest in privacy news, tips, tricks, and security guides to level-up your digital security. If you only want to mask your IP address and don’t need to access the dark web, then going online with a VPN is much easier and faster than using Tor. These domain names are not registered with a central authority but are instead derived from cryptographic keys.
For this purpose, there are so-called “wikis,” which are pages that collect and link to darknet sites. You then have to search for these onion sites within the Tor browser. Additionally, web addresses do not end in “.de”, “.com”, or “.org”, but in “.onion.” To access websites outside the regular web, a so-called onion address is required. The biggest challenge when browsing the darknet is therefore finding or knowing the desired websites. For a local machine configuration, he recommends a computer purchased for cash running Linux, using a local Tor transparent proxy.
Cypher Marketplace
They sell these files for just a fraction of the original cost on the surface web or even share freely, which makes them tempting for people looking for shortcuts. While it might be tempting, remember that downloading such content has serious legal and cybersecurity risks. Unfortunately, the dark web hosts not only explicit but also deeply illegal and disturbing content.
Can I Use A Free VPN To Access The Dark Web?
It is also used by whistle-blowers, journalists, and other individuals who are not involved in illegal activity but need to protect their communications and identities. Through the dark web, users in places of high censorship can also access information and news. The dark web contains content that’s only accessible through networks like Tor.
Enjoy More Secure Browsing With A VPN

Opponents of strict dark web policing sometimes argue that such operations drive criminal activity to even more hidden or encrypted platforms, making detection harder. They may also raise privacy and surveillance concerns, warning that aggressive cyber policies risk collateral impacts on online freedom and legitimate users of anonymity technologies. Additionally, the integration of Bitcoin and other cryptocurrencies has streamlined transactions, eliminating the need for traditional banking systems. This not only enhances privacy but also reduces the risk of financial tracking.
New Shamos Malware On Mac: Beware Of ClickFix Attacks

It is the dark web’s version of Wikipedia with a massive links directory. You will find all the necessary .onion links to access any content or service on the dark web. Check out these best onion sites to access the dark web securely and anonymously.
Is There A Future For Dark Web Marketplaces?
Since the dark web is a hidden and uncontrolled part of the web, there is a high amount of malware infections present there. As a result, you should avoid opening unfiltered sources, torrent sites, and dark web links unnecessarily and downloading every file you come across. Immediately close your entire Tor Browser window (not just that active tab). Note that engaging with the content in any way is not only distressing but could also put you at legal risk. This is because law enforcement often actively monitors these sites.

As these markets continue to grow, they are likely to incorporate even more sophisticated features, such as AI-driven recommendations and enhanced security protocols. The future of darknet drug trade lies in its ability to adapt to technological advancements while maintaining the core principles of privacy and reliability. These features collectively make the darknet a reliable environment for drug trade in 2025, offering users a seamless and secure experience. The leading darknet markets in 2025 offer a wide range of substances, catering to various preferences and needs. This diversity not only attracts a larger user base but also fosters competition among vendors, driving innovation and quality improvement. Buyers benefit from access to a broader selection, ensuring they can find exactly what they are looking for.
Why Is Tor So Slow?
Use it to link your GitHub account, Twitter, Bitcoin address, and Facebook. This .onion link makes it impossible for hackers to impersonate your profile. The good news is that the platform will not see what you copy/paste. Your data is encrypted in the Tor browser before reaching the ZeroBin servers.
Quick Links

However, this feature is only available on iOS, Android, and Windows. The VPN will protect your traffic when you connect with military-grade AES 256-bit encryption. This is high-level protection; no one can intercept your data or activities. A top-of-the-line VPN network that ensures maximum security while accessing dark sites online. This includes military-grade 256-bit encryption reinforced with a 2048-bit DH key and SHA2-384 authentication to ensure your traffic arrives at its destination safely. This adds extra protection since opening Tor itself encrypts your traffic.
Do I Need A VPN If I Use Tor?
It features over 40,000 listings including narcotics, counterfeit items, hacking tools, and stolen data. The marketplace is well-known for its bug bounty programs and robust security mechanisms, including mandatory 2FA. Before these dark web marketplaces were shut down, they sold a range of illegal products, from drugs to firearms. If you’re using a browser like Tor and visiting .onion websites that aren’t accessible through regular search engines or browsers, you’re likely on the dark web. These sites often look basic or outdated, and their URLs are lengthy strings of random letters and numbers. Keep in mind that visiting the dark web isn’t illegal, but engaging in criminal activity there is.

Modern lists also include vendor scorecards, linking directly to market profiles. This eliminates guesswork, as buyers can verify a vendor’s history before entering the market. The combination of updated links and transparent metrics streamlines the entire purchasing process. Markets like Nexus and Abacus dominate due to their consistent link availability and encrypted onboarding. Buyers should avoid direct searches and rely on lists with PGP-signed updates.
Drugs, Hackers, Bitcoins And More: What Is The Darknet And How Do You Access It?
- Unfortunately, others are fake and fraudulent websites that exploit the reputation of the dark web to con people.
- Since then Archetyp has become one of the largest Darknet markets in the world.
- This adds another, more reliable security layer to all of your online activity.
- Activists and government critics prefer to remain anonymous, fearing repercussions if their identities are revealed.
- This means you have to know someone who is already using the platform.
- It assigns a task to the client instead of the server, eliminating server-related vulnerability.
But if you connect to the VPN before connecting to Tor and an IP leak occurs, only the VPN’s IP address will be exposed. I also like that the security guides are user-friendly — the format is easy to scan, complicated terms are explained very well, and there are videos and screenshots. It’s great how the site has a Security Scenarios section too, where it offers personalized security tips for specific audiences (activists, academic researchers, journalists, and more). ProPublica has a clearnet site, but its dark web version won’t see your IP address, so you get better privacy. You can also use its .onion link via the Tor network to access the site in restrictive countries, where it might be unavailable. DuckDuckGo also lets you access chatbots anonymously, has image, video, news, shopping, and other search options.
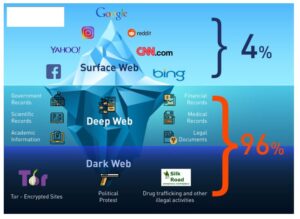
Abacus Market quickly rose to prominence by attracting former AlphaBay users and providing a comprehensive platform for a wide range of illicit activities. Dark web markets have exploded in scale and reach in 2025, becoming the most dangerous hubs for trading drugs, stolen data, and hacking tools. These anonymous marketplaces—operating mainly on the Tor network—are now a primary threat vector for businesses and cybersecurity professionals. The Darknet is a closed network that features websites not discoverable by regular search engines and only accessible through a special Tor browser. Since communication there is encrypted, users remain largely anonymous. This is achieved through a “tunnel system,” where one’s data traffic is meant to be lost within the data traffic of others.
Transactions are encrypted, anonymized, and hardly visible to investigative authorities. Combined with encrypted access via the TOR network, the darknet enables nearly invisible marketplaces for drugs, weapons, data, and much more. Unlike other search engines, it does not collect or share web activities and personal data of users.