The Operation Grayskull investigation launched in 2020, when law enforcement agents noticed a spike in traffic to a dark web site suspected of hosting child abuse material. The dark web child abuse sites eventually attracted more than 120,000 members, millions of files and at least 100,000 visits in a single day, according to an FBI official who spoke with CBS News. It pulls data from different search engines, so it opens you to a world of endless possibilities. With tools like Cyble Vision, it helps organizations stay protected of cyber threats, including dark web monitoring, providing critical insights for better cybersecurity management. The Excavator search engine digs through the depths of the dark web, offering an expansive view of indexed content. One of the oldest and most robust dark web search engines, the Torch search engine is known for being fast, straightforward, and acting as an unblocked search engine with minimal filtering.
ProtonMail — Free & Secure Email Services
As you continue your online journey, keep expanding your knowledge of digital privacy and security. The more you understand, the better equipped you’ll be to navigate safely and confidently, no matter where your curiosity leads you. With that in mind, let’s explore some of the most reliable dark web search engines available today to get you started.
Accessing the dark web isn’t like surfing the web everywhere else online. Many dark web links could get you mixed up in some kind of criminal activity of another, whether you’re looking for it or not. The deep web is rife with sales of illicit drugs, weapons, and goodness knows what else, and steering clear of these nefarious web pages is easier said than done.
- In practice, we found very little use of VPN Over Tor and saw no significant advantages.
- However, if you’re looking to trade or buy something, the risk of scams increases exponentially.
- However, it\’s important to note that Tor doesn\’t automatically discover Dark Web websites for you.
- You’re also open to threats like end-to-end correlation attacks, so while Tor is a lot more secure and private, it’s by no means completely safe.
- Although the underground internet world is rife with everything bad, it also hosts positive elements.
Table Of Contents
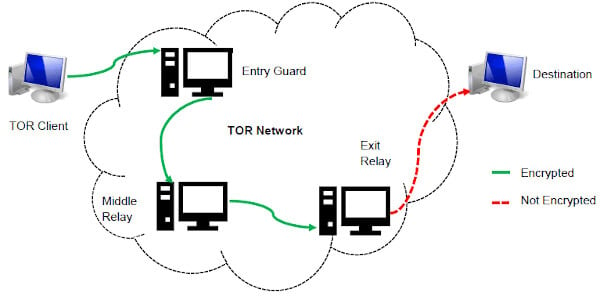
Political dissidents in a oppressive country could use the dark web to communicate and organize. Whistleblowers can leak secrets on the dark web using sites like The New Yorker’s Strongbox, reducing the risk they’ll be tracked down. Even Facebook offers its website as Tor hidden service, making it more safely accessible to people in countries where Facebook may be blocked or monitored. You can tell you’re on the dark web if you’re accessing websites with .onion addresses on the Tor Browser or a similar anonymity network. These sites aren’t accessible via standard web browsers or search engines.
Keeper is the first and only password management application to be preloaded with mobile operators and device manufacturers including, AT&T, Orange, America Movil and HTC. Keeper has millions of consumer customers and the business solution protects thousands of organizations worldwide. Dark web search engines exist, but even the best are challenged to keep up with the constantly shifting landscape.
How Do I Access Onion Sites?
- This is no different from the “.net” or “.com” of the regular Internet.
- Cybercriminals often disguise malware within legitimate-looking files to trick users into compromising their own security.
- Users have access to settings that allow them to control search parameters and privacy settings, further enhancing the personal security and customization of the search process.
- There are several email and IM services which you can use, and it’s highly recommended to pick one if you want to step up your dark web game.
- Switzerland-based Proton (formerly ProtonMail) is one of the most secure email services, and has a reputation for not logging IP addresses.
The sharing of illegal pornography and discussion of illegal sex acts account for a significant portion of dark web traffic. The extent of the problem became clear in 2015, when the FBI shut down a dark web site on Tor named Playpen that hosted 23,000 sexually explicit images of minors. Not all mass thefts of data facilitated by the dark web have been motivated by money. The publicizing of Snowden’s actions led to a global spike of interest in Tor and a resulting rapid expansion of the network’s user base. We strongly advise against accessing the dark web, even for ethical purposes, unless you’re fully informed about the dark web risks and have enhanced your device’s security.
How To Find New, Active Dark Web Links
To help find functioning .onion URLs, look to dark web directories and forums — Reddit users recommend tor.taxi, tor.watch, daunt.link, or one of the Hidden Wikis. Unlike the publicly accessible surface web, the deep web includes sites requiring login credentials but is still accessible via traditional browsers. The dark web is a small, hidden subset of the deep web that requires special tools to access. For businesses, the dark web represents a critical security threat. Stolen credentials, trade secrets, and personal customer information are frequently sold on dark web marketplaces. Conducting regular cybersecurity assessments and implementing security gap analyses are essential measures to protect sensitive data.
What Are Tor Onion Services?
This service helps protect your primary email when signing up for .onion services. I found it especially useful for testing new services without risking my main email address, though messages expire after 24 hours. The key takeaway is that the dark web is part of the deep web, but they’re not interchangeable. As for the dark web, it’s intentionally hidden, encrypted, and made anonymous. As you can probably imagine, that’s exactly what threat actors on the internet want to hide their nefarious deeds. Onion sites are websites on the dark web that use the ‘.onion’ top-level domain.
Related Articles From The Safe Browsing Section

We test each product thoroughly and give high marks to only the very best. We are independently owned and the opinions expressed here are our own. Virtually anything you can buy on the surface or clear web you can also find on the dark web. Books, video games, apparel and rare collectibles are some of the legal items you can buy on dark web commerce sites.
The New York Times — Globally Recognized News Coverage
Apart from the dark web markets that are operating online today, some raided platforms influenced many markets. It has a bidding feature, with new batches of stolen data being frequently added. Security researchers have been monitoring forums within the cybercriminal underworld to investigate the leading markets operating in 2024. The second category consists of data stores, which specialize in stolen information.
The service doesn’t require personal information to create an account and works seamlessly through Tor. I found in my tests that all features work identically to the regular version. TorLinks maintains one of the most reliable directories of verified .onion sites.
Well, now it’s time to fire up Tails and do a little bit of tinkering. Chill, because nobody will ever find a record of you ever fiddling around the darknet. Note that Tails’ installation package is the .img format, which means that you’ll need software capable of burning images on your thumb drive. Tor relays are servers run by volunteers, designed to keep your activities private and untraceable. We’re a nonprofit organization and rely on supporters like you to help us keep Tor robust and secure for millions of people worldwide.
Cryptocurrency, particularly Bitcoin, plays a significant role on the Dark Web. Many transactions conducted on the Dark Web involve the exchange of cryptocurrencies, as they offer a level of anonymity that traditional currencies cannot. For example, the Freedom of Information Foundation has long advocated for the use of the Dark Web in enabling free speech in repressive regimes. The Dark Web often carries a stigma, primarily due to its association with illegal activities. However, it also serves as a tool for privacy-conscious individuals, activists, and others who need to operate in secrecy.
IV Verifying The Authenticity Of Links And Resources
Not to mention that anonymity safeguards won’t protect you from other threats like hacking and malware. Social media platforms like Facebook and news sites like the BBC and ProPublica have also waded into the dark web’s waters. These legitimate media companies keep a presence on the dark web to help users who might, for a variety of reasons, have difficulty accessing their content on the open web. In the internet’s darkest corners, a myriad of hidden websites cater to an array of needs and interests.



