For example, perpetrators of trafficking and cyber attacks use the dark web to disguise their actions. The system is designed to provide enhanced security and privacy features. Its key features include kernel hardening, application firewall, package security, filesystem encryption, meta-proxy encryption, and binary integrity. Furthermore, it’s critical to understand that Whonix is not a stand-alone browser. It is a component of Whonix, an operating system that functions as a whole inside a virtual computer.
Best Tor Sites Available On The Dark Web – Quick List
This website allows you to type in your email address or phone number and see if it’s been compromised in any data breaches. If your information has been compromised, then it’s likely that your phone number is also on the dark web. For a number of technical reasons, it’s much faster and more reliable than Tor.
But the site’s owners have repaid 50% of the thousands of victims affected by waiving wages and donating commissions. The Silk Road bust has hit darknet user and vendor confidence, however. “There isn’t a feeling of invincibility that was pervasive last year at the same time,” said Cristin.
Official Mirror Links
New coins also pop up frequently, often designed specifically for fraud and scams, such as rug pulls and pump and dump schemes. Nearly all of the above criminal activities involve cryptocurrency as a means of paying for illicit goods and services on dark web markets. But the dark web is surprisingly easy to access, and there are some legitimate uses for its heightened anonymity features. Plus, it’s a great place for the good guys to get intel and track down criminals…if it’s accessed safely, with all necessary precautions.
PRIVACY ALERT: Websites You Visit Can Find Out Who You Are

Sci-Hub gives access to millions of scientific papers, mostly ones from behind paywalls. However, due to copyright infringement, Sci-Hub is considered illegal and banned in many countries. A favorite of journalists and their anonymous sources, SecureDrop makes it easy to share confidential information without revealing your identity. Many news publications, like the ones listed above, have a SecureDrop on their .onion sites.

How To Use A VPN To Access The Dark Web
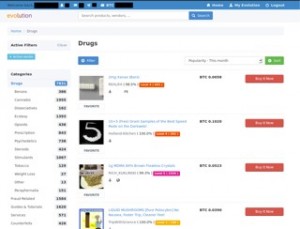
Genesis Market and BidenCash, two top dark web marketplaces, were also shut down in 2023 and 2025, respectively. This can include everything from full names, email logins, and passwords to credit card details, social security numbers, and bank account information. The cybercriminals trade even sensitive documents, such as medical records, passport information, and driver’s licenses. Whether you want some pharmaceutical products (drugs) or digital items, you will probably find the products here, and that too at affordable prices. Vice City listens to the problems faced by its customers and vendors and solves them so that they can keep using the platform with ease.

Dark Web Websites: How To Access Them Safely

Unlike many imitators, this is the official Hidden Wiki that maintains a curated directory of legitimate .onion services. During my testing, I found its categorized index particularly helpful for discovering trustworthy sites across various topics. Though some are scam or fraudulent listings, the wider growth pattern is clear. There is now even a darknet search engine, Grams, as well as a central repository carrying reviews for all darknet drug dealers, called the Hub. It’s a breeding ground for illegal activity and a haven for cybercriminals.
Ways Small To Midsize Businesses Can Stay Safe In The Cloud
- But they’ll only work in the Tor browser, while connected to Tor.
- Offering books for free, shadow libraries face the morality question of copyright vs. access to information and knowledge.
- The majority of the users on the dark web use the Tor (The Onion Router) browser.
- Bear in mind too that laws about freedom of speech and censorship vary from country to country, which is part of the reason the dark web exists in the first place.
- If the above average Joe’s explanation isn’t enough for you, below are some legitimate reasons to use the Dark Web in a bit more detail.
I found it especially useful for testing new services without risking my main email address, though messages expire after 24 hours. Your ISP, and possibly the authorities, may decide to start monitoring your activity more closely to look for threats or illegal activity. That’s why we always recommend using a VPN over Tor—even if you feel you have nothing to hide.
Enter A Darknet Web Address
Here are some of the now-defunct dark web markets that were notorious for cybercrime. Launched in 2023, STYX focuses on financial crime, providing stolen credit card data, hacked bank accounts and access to various cryptocurrency laundering tools. Nexus Underground Market operates as an online marketplace within the depths of the darknet, standing out as a comprehensive platform.
How To Access The Dark Web?
Unfortunately, others are fake and fraudulent websites that exploit the reputation of the dark web to con people. Moreover, malicious actors can attempt phishing scams to steal your data and identity for extortion. Lastly, the dark web is the portion of the deep web that is generally inaccessible and is much larger than the surface web. It relies on P2P connections and requires specialized tools and software. Tor and I2P are the two commonly used tools for accessing the dark web to provide anonymity.
DarkBlue’s CluesAI tool saves you time by generating automated intelligence reports for running down leads and deanonymizing bad guys. CluesAI works by scanning relevant records and revealing relationships between data points like usernames, contact information, cryptocurrency wallets, and more. Yes, many organizations monitor the dark web for cybersecurity intelligence—always in line with legal compliance.
The Surface Web
The dark web, which is what I’m discussing here, is a small subset of the deep web, and refers to websites that are specifically trying to stay out of sight. With rising online privacy concerns in the current digital age, the Tor network’s anonymity is becoming essential. It is a good way to prevent third parties from tracking online activities.



