Even with Tor and a VPN, you’re not fully protected unless you also lock down your behavior. Most dark web leaks happen when users skip basic safety steps or reveal too much without realizing it. Use the tips below to patch common blind spots and avoid easy-to-make mistakes. Tor has an in-build slider which lets you adjust the level of security. This means that the JavaScript will be disabled by default on every website and some symbols and images will not be displayed.
Official Websites And Documentation
We already went through VPNs, anonymizing web browsers, and disposable operating systems, so I won’t bother reminding you about those. Sure, it’s not as secure as the clear web version, but it’s there and totally legal to use. Hidden Facebook is hardly the only social media client on the dark web.
How To Handle And Prevent Online Harassment
Instead of ending in .com or .co, dark web websites end in .onion. That’s “a special-use top level domain suffix designating an anonymous hidden service reachable via the Tor network,” according to Wikipedia. Browsers with the appropriate proxy can reach these sites, but others can’t.
Minimize Or Rescale Your Tor Browsing Window
However, your information is vulnerable without a VPN since it has only Tor’s layered encryption as protection. A solution to this is to set up a VPN within your router, effectively encrypting your entire connection. If you feel a browser just won’t cut it and want to keep your dark web browsing activity as private as possible, Whonix might be for you.
Should I Use The Tor Browser For Everything?
It is made up of two virtual machines – a Gateway and a Workstation. All traffic must always go through the Tor network through the Gateway. This architecture protects your IP address even when the Workstation is before malware that may compromise it. While not all Tor users are deep, dark web users, over 90% of the users who are interested in accessing the deep, dark web use Tor to access it. To access the dark web, you must have specialized software, such as the Tor Browser. It creates a space for staying anonymous, which itself is kind of a double-edged sword.
Being the unregulated part of the internet, the dark web is full of illegal activities. The chances of opening websites with malicious, inappropriate, or illegal content are very high, especially if you don’t know the exact .onion website you wish to visit. It offers a unique feature where your device traffic is first sent through the VPN and rerouted through the Tor network. This VPN provides access to specialized Tor over VPN servers, enhancing privacy and security.
- Responsible use protects your privacy while staying within the law, so it’s a safe place to browse for real privacy reasons.
- This article aims to give a thorough analysis of the top ten darknet browsers for 2023, rating them according to privacy, security, and usability standards.
- Services like Random Chat connects you with random people using the same service.
- We discussed the importance of setting up Tor Browser correctly, ensuring security and anonymity, and navigating the dark web safely.
- It can only be used to access the content uploaded to the Freenet, which is a peer-to-peer distributed data store.
- Do not install the browser from any other location, as it may be infected with spyware or other nefarious programs.
This group consists of a populace whose actions on the internet would rapidly lead to imprisonment or fines. Such people can be opposition figures from dictatorship-led countries, politically oppressed guys, whistleblowers, or journalists. The dark web is rife with cybercriminals who offer their services either as individuals or as part of a group. These groups include Mazafaka, Trojanforge, hack forum, xDedic, and dark0de.
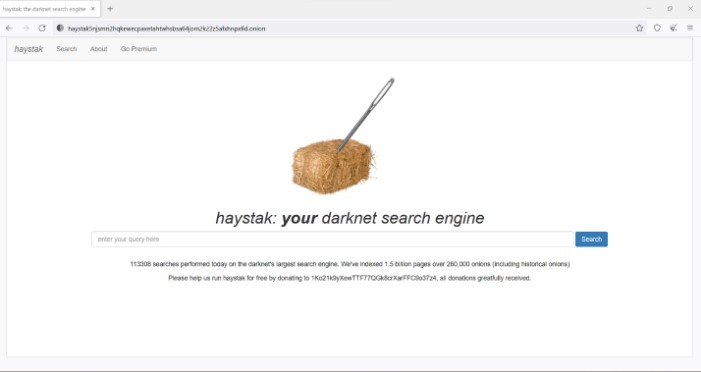
Do I Need A VPN To Access The Dark Web?
For example, you could find a passport from a UK citizen there for under a million dollars. Therefore, to ensure that you stay anonymous on the dark web, you can use Bitcoin mixers (also known as cryptocurrency tumblers) or opt for a privacy-focused coin such as Zcash and Monero. The best way to clear the traces is by installing the Amnesic Incognito Live System (TAILS) – a unique Debian-based version of Linux that removes the user activity on the computer. Due to its hidden nature, the dark web is also famous for the names underground internet and black web.
What Is Digital Inclusion?
Even if your device is stolen or hacked, your sensitive information will remain secure. Now you’re probably asking, is the Deep Web and Dark Web even legal? There are many websites that exist within the Dark Web that provide illegal products or services, but generally speaking the Deep Web and Dark Web in and of themselves are legal. They can actually be a fantastic resource of knowledge and power when used mindfully.
- Setting up I2P requires more configuration on the user’s part than Tor.
- Another reason you don’t want to use the Tor Browser for your daily web browsing is that it draws attention to you.
- With Tor installed on your PC or mobile phone, you’ll be able to browse active onion websites and protect your online privacy and anonymity.
- We recommend that you use only the Tor browser to access the deep, dark web, if you must.
Prior to joining CrowdStrike, Baker worked in technical roles at Tripwire and had co-founded startups in markets ranging from enterprise security solutions to mobile devices. He holds a bachelor of arts degree from the University of Washington and is now based in Boston, Massachusetts. The VPN provides data encryption and routes your data through remote servers to help mask your IP address and location. Thus, it successfully prevents anyone from snooping during your activity. The VPN has a vast and well-established network, with 6,000+ servers spread across 111+ countries.
One more thing before we move on – accessing the dark web is LEGAL. Selling drugs or hiring a hitman to kill your ex will get you into trouble. However, you can browse forums, watch videos, and chat with other people just fine. This is usually done to prevent tracking and website shutdowns typical for this part of the internet.
Disadvantages Of The Tor Browser
The Darknet offers a place of free expression where not even a chunk of these limitations exists. They exchange sensitive information and data and, at times, have to risk their lives or that of their informant if they don’t share data under the safety of the deep web. Information on the dark web is not meant for public consumption, and the dark web protects personal data intended to be private. Law enforcement agencies frequently target sites that distribute child pornography. For Example, In May 2021, authorities in Germany brought down Boystown, a child pornography network with more than 400,000 registered users. Several pedophile chat sites were also dismantled, and four people were detained, one of them a Paraguayan suspected of running the network.
Step 4: Access I2P Sites (Eepsites)
Library Genesis offers a search engine for collections of books on such topics as computers, business, technology, and more. These are only a few of the .onion search engines that are available. Onion sites are websites on the dark web that use the ‘.onion’ top-level domain.