Users should be well aware of these risks before venturing into this part of the internet. In 2002, the dark web grew significantly when researchers supported by the US Naval Research Laboratory built and released the Tor network. At the time, the internet was still young, and tracking people was easy while staying anonymous was not. The Tor network allowed safe communication channels for political dissidents and American intelligence operatives around the world. Regular dark web visitors know that it’s possible to exploit the sketchy reputation of the space and the services offered.
- Here are our favorite choices that work well and support Tor Over VPN perfectly.
- Tor, short for “The Onion Routing project,” is a free, open-source network built to protect online privacy and enable access to the dark web.
- Let’s discuss some more differences so you can easily distinguish them.
- With this setup, you connect to your VPN first, then open Tor Browser.
- Tor Browser already comes with HTTPS-Only mode, NoScript, and other patches to protect your privacy and security.
Remember, while the dark web hosts a range of content, accessing illegal materials or services is, well, illegal. This essentially just makes certain that your VPN is working and that your personal IP address isn’t exposed for malicious actors prowling the dark web. To conduct this check, just turn on your VPN and head over to ipleak.net and dnsleaktest.com to see if the IP address displayed is the one from your VPN. There are a huge number of overlay networks to choose from, but some of the most popular include Tor, Freenet, and Riffle. You’ll need an overlay network to facilitate your dark web access.
A VPN will give you an extra layer of protection and anonymity, making it much safer to explore the dark web. Unlike Tor, however, it cannot be used to access the public internet. It can only be used to access hidden services specific to the I2P network. I2P cannot be used to access .onion sites because it is a completely separate network from Tor. Instead, I2P uses its own brand of hidden sites called “eepsites”. Even when using security measures and your common sense, accessing deep web content still poses a risk.
Can I Go On The Dark Web On My IPhone?
This website allows you to type in your email address or phone number and see if it’s been compromised in any data breaches. If your information has been compromised, then it’s likely that your phone number is also on the dark web. Freenet is still an experiment designed to resist denial-of-service attacks and censorship. Due to all the nodes that your traffic passes through, Tor by itself significantly limits bandwidth.
Can I Access The Dark Web With The Tor Browser?

Although browsing the dark web is not illegal, it contains unsavory activities that can expose you to danger. Remember that any website engaging in illegal activities such as drug trafficking, weapons sales, hacking, and human trafficking violates international laws and, therefore, is illegal. Only access the dark web with both a VPN and the Tor Browser active. Avoid altering any security settings in Tor that could reduce your protection. For more advanced use, Hyphanet allows you to create and host your own freesites, participate in forums, and communicate anonymously with other users. These features are accessible from the Freenet interface under the “Community” and “Tools” sections.

How To Access The Dark Web Safely And Securely
A key aspect of this configuration is the handling of JavaScript. Disabling JavaScript, especially on non-HTTPS sites (in “Safer” mode) or entirely (in “Safest” mode), is a widely recommended security practice when browsing the dark web. JavaScript can be exploited by malicious websites to track users, reveal their real IP address, or deliver malware. Norton 360 Deluxe provides a comprehensive suite of protection that can help block malware and dangerous links in real time, and even detect scams using cutting-edge AI detection. Plus, it features a built-in VPN to encrypt your connection, hiding your IP address and online activity, for more anonymous and private browsing.
Swap Data In Countries That Censor The Internet

Bear in mind too that laws about freedom of speech and censorship vary from country to country, which is part of the reason the dark web exists in the first place. DuckDuckGo is the default search engine inside the Tor browser, and once you turn on the Onionize toggle switch in the search box, you’re able to use it to find dark web links. These typically come with “.onion” after them, rather than something like “.com” as on the standard web. Tor is like the public-facing door to the dark web, and there are even mobile apps for Android and iOS.
Step 4: Configure Basic Settings

If you engage in illegal activities or access illegal content that could implicate you in a criminal offense, you may face serious legal consequences, including fines and imprisonment. When you visit dark web sites, even if you don’t have any ill intentions, you support the dark web ecosystem, which serves as a medium to conduct various illegal activities. The dark web hosts various types of illegal content, such as stolen data, child exploitation material, and prohibited items. As an average Internet user, you may accidentally stumble upon such content. Your access to illegal content, even if it is unintentional, can violate laws in many countries.
To further enhance your safety, you can use dark web scanners to know if your personal information has been compromised. If you decide to visit these marketplaces, exercise extreme caution and remain aware of the legal implications of your actions. Always prioritize your privacy by not sharing personal information, and use additional security measures like a VPN to further protect your identity. There is only one official download site for the Tor browser, and that is torproject.org.
Yes, many organizations monitor the dark web for cybersecurity intelligence—always in line with legal compliance. Analytics Insight is an award-winning tech news publication that delivers in-depth insights into the major technology trends that impact the markets. The content produced on this website is for educational purposes only and does not constitute investment advice or recommendation. Always conduct your own research or check with certified experts before investing, and be prepared for potential losses. Opinions expressed herein are those of the authors and not necessarily those of Analytics Insight, or any of its affiliates, officers or directors.
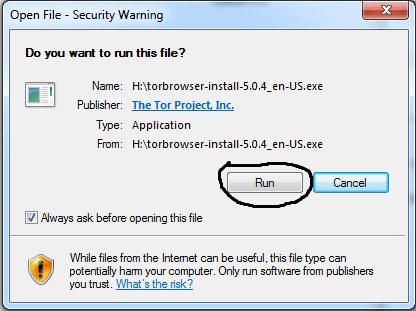
Step 2: Install I2P

Engaging with these sites, even inadvertently, can expose individuals to serious legal consequences, including criminal charges. Law enforcement agencies worldwide monitor the dark web, and accessing these illicit markets, even out of curiosity, can draw unwanted attention and legal scrutiny. The dark web is full of malicious actors, cybercriminals, and other people who are looking to prey on curious but unprepared dark web browsers. By defining your goal and purpose, you won’t find yourself wandering down the dimly lit corners of the dark web, and you can stay on the path you set out for yourself.
Manually implies clicking the Connect button each time you open Tor, while automatically means an automatic connection whenever you open the Tor browser. Open the downloaded file on your device to begin the installation process. The process is similar to installing any other software – follow the on-screen instructions and wait for the installation to complete. Once complete, you can add Tor to your shortcuts menu for easy access. However, this does not provide any extra security for your device or information.
Malicious actors often target browser plugins to steal website credentials or install malware on unsuspecting devices, so Tor sidesteps these risks altogether. Always verify a site’s legitimacy before visiting – onion addresses are long, random strings, making it easier for malicious actors to create lookalike addresses for phishing. A little typo can lead you to a clone designed to trick users into handing over sensitive data.
The Hidden Wiki
You can change the IP address the Tor network assigned to you by connecting to different servers — to do that, first click the padlock icon next to the site’s URL bar. Next, hit the New Circuit for This Site button to connect to a different server chain. Repeat this process until you get an IP address from your desired country. You can now start surfing the web while connected to the Tor network. Access any site you want as you normally would on your regular browsers. Just keep in mind it might take a bit longer to connect to a site due to Tor’s slow speeds.
I personally think the Tor browser is only good for surfing dark web links, while VPNs have many more use cases — they’re great for streaming, torrenting, gaming, and bypassing censorship. And while both Tor and VPNs provide security and privacy, I think VPNs are better because Tor has some security issues. However, the first Tor server you connect to can see your real IP address — if a malicious actor operates it, they could collect it and use it to track your location or online behavior. While Tor is legal in most countries, it can also be used for illegal purposes.