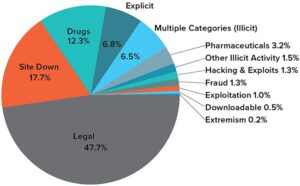
The CIA (Central Intelligence Agency) provides a .onion version of its website, enabling individuals to bypass restrictions to access its content from anywhere. This platform allows visitors to anonymously explore the World Factbook, submit information, apply for jobs, and perform any other actions available on the CIA’s main site. The Hidden Wiki is the dark web’s unofficial Wikipedia, where you can find “.onion” links for many dark web pages, services, and other content. The Hidden Wiki doesn’t discriminate, so if you randomly start diving into the onion sites listed, you may come across objectionable or dangerous material. OnionLand functions as both a dark web search engine and a deep web search engine, offering a smooth user experience and access to thousands of hidden services. Designed to be hidden from conventional search engines like Google or Bing, the dark web is a portion of the internet.
How To Access onion Sites Safely

AVG Secure VPN masks your IP address from other internet users, the websites you visit, and even government surveillance. And thanks to ultra-secure, end-to-end encryption, your online activity is obscured. While this doesn’t tell the exit node what your original IP address or your geographical location is, it could spy on your activity if the website you’re visiting isn’t a secured HTTPS website. The Tor browser provides access to “.onion” websites, which are Tor hidden services that you can only access through the Tor browser. You can access these websites without worrying about someone snooping on a Tor exit node, offering more private browsing of what is known as the deep web.
- The social media giant is also aware of the many attempts by repressive regimes to restrict its access.
- In case of an attack, you can be sure that any of the data or information stored on your main computer will be safe.
- It was initially created to provide additional security and eliminate cryptocurrency theft.
- It offers features like encrypted communication for chats and file sharing, making it popular with privacy-conscious individuals.
- The websites on this part of the internet range from benign to very malicious.
In “safer” mode, JavaScript is disabled on HTTP sites, some fonts are disabled, and all audio and video won’t run automatically, you’ll have to click to play. Slide up to the “safest” level, and as well as those settings, JavaScript is disabled on all sites. While the Tor Project does its best to anonymize your browsing as much as possible, it’s not a perfect solution. One major vulnerability it’s unable to account for is something called traffic-analysis attacks.
- Major news outlets like The New York Times, The Economist, and The Guardian host SecureDrop instances on the dark web to give sources a safe, anonymous way to share sensitive information.
- The Hidden Wiki is a longstanding directory of dark web sites that offers a way to browse onion services.
- And if you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.
- Offering books for free, shadow libraries face the morality question of copyright vs. access to information and knowledge.
Download Tor Browser
Clicking on random onion links is quite risky and isn’t recommended. A random dark web link can lead you to malicious software, phishing sites, and illegal content. Apart from the best onion sites listed here, you must be careful with the Tor pages you visit.
How To Browse The Dark Web Legally
Keybase is a fantastic onion website that lets you cryptographically bring your different online identities together. The .onion site has thousands of downloadable comic books ranging from niche to mainstream. As with the Imperial Library, you should be aware of copyright infringement. It aims to advance research on terminal illnesses like cancer with access to unbiased scientific publications. Sci-Hub is a massive database that eliminates the barriers to getting scientific knowledge.
How To Uninstall The Tor Browser
Below are a few key functionalities of the browser, and additional ones can be found in the Tor Browser’s official design document. When your traffic first leaves, Tor will modify it so that only the source (your computer) and the immediate destination (the entry node) can be known to anyone who might intercept it. Thus, through the dark web, you can buy illegal substances, order a hitman, watch underage pornography, and engage in all sorts of illicit activities. Needless to say, we don’t recommend indulging in this nasty side of the darknet. Furthermore, there are news portals and marketplaces where you can buy drugs, guns, stolen/forged passports, PayPal accounts, hardware, software, and many other stuff.

Users Who Read This Also Read:
It’s, ironically, more conspicuous than using popular browsers and sites. Because of its anonymity, the dark web is filled with illegal services and is used by numerous criminal groups, including ransomware gangs. It is also used by whistle-blowers, journalists, and other individuals who are not involved in illegal activity but need to protect their communications and identities. Through the dark web, users in places of high censorship can also access information and news. To make its journalism more accessible to readers around the world, the New York Times launched its onion service in 2017. You won’t find any “hidden” stories here—it’s the same content as the normal web edition—but users in countries with government censorship will appreciate having a secure way to access it.
No Protection Against Malware
The easiest way to use Tor is through its dedicated browser, which is available for Windows, MacOS, and Linux (it can be run from a USB stick if you don’t want to install it on your computer). The Tor browser is based on Firefox but disables plugins that could compromise your privacy and security. Info like your name or email address never needs to be shared on the dark web. You should also limit the number of financial transactions you make on Tor banking portals. Enable MFA wherever possible to protect your accounts from unauthorized access. This space for private free speech also carries the risk of exposing you to harmful content.
Needless to say, it has a security audit from Deloitte, backed by a plethora of security features that millions of users enjoy. All three providers are super reliable and capable of keeping you safe and secure while you browse the dark web. Once you’re there, you’ll be able to enjoy 360-degree protection against hackers or other malicious entities on this part of the internet. If you ask me, this is the only proper way of enjoying the darknet without worrying about possibly corrupted Tor nodes.

Tordex is an uncensored dark web search engine that is accessible through the Tor browser. It allows you to suggest new onion sites for indexing and provides a unique feature displaying the last 5 public searches, offering insight into popular trends on the dark web. While Tordex aims to provide unrestricted access to dark web content, you should exercise caution as the lack of censorship may lead to exposure to sensitive or illegal material.
In addition to providing anonymity, Tor allows users to access the dark web. While the dark web is used for illegal activities, the service is also valuable for those who live in countries where freedom of speech and access to information is restricted. Beyond that, many legitimate organizations, such as the New York Times, have a presence on Tor. Their URLs end with .onion, distinguishing them from regular websites.
Accessing the Dark Web using the Tor Browser is not just about exploring hidden parts of the internet—it’s about understanding privacy and cybersecurity in the modern world. Cybersecurity Student → Conducts research on privacy tools → Accesses ethical hacking forums (legal) using Tor. When you’re done surfing or shopping on the dark web, don’t forget to shut down Tails.
A favorite of journalists and their anonymous sources, SecureDrop makes it easy to share confidential information without revealing your identity. Many news publications, like the ones listed above, have a SecureDrop on their .onion sites. Facebook is aware of attempts by many governments to restrict access to a tool that allows strangers across the web to talk and collaborate freely. While its .onion address doesn’t make it much easier to maintain an anonymous account, it does make Facebook more accessible in places where it’s censored. mark it means it has been verified as a scam service and it should be avoided. Other types of applications can be “Tor-ified”, i.e., made to connect to the internet through the Tor Network.}
Coming across these sites isn’t a matter of searching Google – you’ll need to find specific links. To enhance safety while browsing the dark web, it is essential to use a VPN like Forest VPN before connecting to the Tor Browser. A VPN adds an extra layer of encryption and hides your IP address, protecting your privacy from potential surveillance. Before venturing into the dark web, it’s vital to connect through a VPN like Forest VPN.
Torch is funded primarily through advertising—purchased in BTC, of course—which is why you’ll find the front page blanketed with old-school banner ads of dubious origins. Founded by security researcher Juha Nurmi, Ahmia is essentially a list of “hidden” sites that do want to be found. Onion sites are “crawled” and added to the list provided their “robots.txt” file permits it, and if it is not on their blacklist of sites with abuse material. Site operators can also submit their own .onion sites for indexing. When you try to connect to a .onion website, Tor will route your traffic through three or more randomly chosen nodes before it reaches your destination website.