
In a world of bulk data collection, surveillance, and personalized ad tracking, it’s up to us to take control of our personal privacy. This information can be used to target ads and monitor your internet usage. You can either sell or buy goods on the dark web, but both present difficulties. These high levels of anonymity increase the opportunity for the “bad guys” to sell drugs, stolen IDs, credit cards, weapons, and many more compromised products or information.
Navigating The Dark Web: Do’s And Don’ts
For example, DuckDuckGo is the most popular but often shows repetitive results and is sometimes unrelated to the question. Since Tor has to pass your traffic through several nodes, it will slightly slow your speeds. You can use the Smart Location feature for the fastest connections. ExpressVPN is an excellent choice for Tor and accessing the Dark Web. It has a proprietary onion site in the Tor network to give you safe access even if your country restricts VPN usage.

Cybersecurity Best Practices For Protecting Your Digital Assets
When using Tor Browser, it is important to note that while it provides a higher level of anonymity, it does not guarantee complete protection. It is still possible for malicious actors to monitor online activities, especially if users engage in unsafe browsing practices or download suspicious files. Tor Browser is a web browser that allows users to access the internet anonymously. Cybercrime services, such as hacking tools and stolen databases, are available for hire, creating a marketplace for illicit online activities.
Tor And Onion Routing Explained
That said, a few standout free VPNs are safe enough to pair with Tor, especially if you’re just browsing, downloading PGP keys, or checking out .onion sites with a light footprint. In this guide, we’ll walk you through the best free VPNs that actually work with the dark web. We’ve tested each one to see which keeps your identity airtight, your speeds usable, and your Tor sessions under the radar.
How To Choose The Right Dark Web Monitoring Tools For Your Business?
- Importantly, not all users of these spaces are criminals—some are security professionals, journalists, or researchers trying to understand threat actors or investigate breaches.
- As always, protect yourself from online threats with mobile Android security or iOS security software.
- Proton Mail is an anonymous email service that operates an onion site.
- The trick with these onion websites is their accessibility, which is made possible only with Tor.
- Upon opening the Tor website, you will be presented with various download options for the operating systems that Tor supports, including Windows, macOS, Linux, and Android.
ZDNET tested the best VPNs available based on speed, number of servers, security features, price, and more. ExpressVPN is our pick for the best VPN overall, thanks to its fast and reliable connection and the wide range of platforms it works on. A VPN will mask your location and stop the online breadcrumbs that can lead back to you.

Tips For A Safe Dark Web Experience
Choose a reputable VPN service with strong encryption and a no-logs policy to ensure maximum privacy. Remember, the Tor browser connects to the internet differently than regular browsers in an attempt to increase your anonymity online. Yes, if you don’t use a VPN, your ISP can see that you’re connecting to the Tor network.
Dark Web Search Engines
If your device is infected with malware, read our guide to remove malware from your computer. Using a VPN alongside Tor adds an extra layer of security by hiding your IP address from Tor entry nodes and encrypting your traffic. This prevents anyone—including your ISP—from knowing that you’re using the Tor network. The Deep Web includes unindexed content like private databases and password-protected sites accessible with standard browsers.

The same applies to downloading files, which often contain tracker elements. You should avoid downloading files via Tor to maximize your anonymity. For example, in Safer mode, JavaScript is turned off on non-HTTPS (insecure) sites, but in Safest mode, JavaScript is turned off entirely for all sites. Images load normally in Safer mode, but some complex images may not load in Safest mode. To connect manually for the first time, click on the Connect button on the homepage and wait for Tor to establish a connection. Since its public release, researchers have discovered various vulnerabilities in Tor, which have been quickly patched.
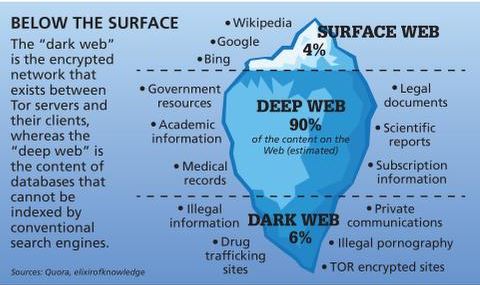
The terms “deep web” and “dark web” often appear interchangeably in headlines, but they describe very different slices of online reality. The deep web simply encompasses everything that sits behind a login, paywall or other access control—corporate intranets, streaming queues, medical records, even your private Google Docs. These pages rely on the same protocols and domain names as the public Internet, yet search‑engine crawlers cannot reach them because authentication gates keep casual visitors out. In most cases, the deep web exists to protect privacy, enforce intellectual‑property rights or comply with regulations.
Words Of Caution When Using Dark Web Sites
Freenet was originally intended to provide a way to anonymously interact online, providing ways to communicate, exchange information and files, and to otherwise communicate incognito. The dark web addresses are a randomly-scrambled sequence that generates URLs, mostly hard to remember ones. For example, the URL of Silk Road is rather unintelligible and may look something like “gan4arvj452janndj4a76.onion”. So, even though it does exist on the internet, Google doesn’t index any of these pages or content. With your VPN active and Tor installed, you’re now ready to connect.
The dark web refers to sites that are not indexed and only accessible via specialized web browsers. Significantly smaller than the tiny surface web, the dark web is considered a part of the deep web. Using our ocean and iceberg visual, the dark web would be the bottom tip of the submerged iceberg. That said, a significant chunk of U.S.-based activity on the dark web still revolves around illegal marketplaces—selling things like stolen data, counterfeit documents, and even drugs. Lastly, keeping the Tor browser and any security software up to date is important for staying ahead of potential vulnerabilities. By following these tips, individuals can enhance their safety and privacy while exploring the Dark Web.
- I2P’s most attractive angle is to access its own internal eepsites, which are its version of .onion sites.
- However, while visiting the dark web itself isn’t against the law, engaging in illegal activities there is.
- Unfortunately, it’s slower than NordVPN and ExpressVPN but overall, its performance is admirable in practice.
- It offers outstanding privacy features and is currently available with three months extra free.
- Keep your personal details secure by using aliases and anonymous email accounts when creating dark web accounts.
- Tor is a browser engineered for extra security and privacy, and can be used to navigate the normal, surface web as well as the dark web.
The Biggest Crypto Exchange Hacks: How To Make Sure You Protect Your Crypto Against Hacks
While ProtonMail has a solid commitment to privacy, its location has caused problems for users in the past. In 2021, it was forced by the Swiss courts to begin logging the IP addresses and browser fingerprint information of one of its customers. Let’s take a closer look at the best VPNs you can use to safely access the dark web.
The “onion routing” technology underpinning the dark web was developed by researchers at the U.S. Initially designed for secure military communications, it evolved into a broader tool for online anonymity, later expanding to public use with the Tor network. Another challenge of finding dark web sites is that they don’t often last long. Many sites become defunct quickly, either because they are shut down due to illegal activity, their founders lose interest, or they change addresses and names to avoid detection. Next, select a dark web search engine like DuckDuckGo that can help you find dark web websites that cannot be indexed by traditional surface web search engines, such as Google or Bing. Many dark internet users favor Tor which uses a network architecture originally developed by the U.S.

These websites use special encryption protocols and are accessible only through anonymizing tools like the Tor Browser. I2P is a private network built for secure, anonymous communication. Instead of the onion routing Tor uses, I2P relies on unidirectional tunnels and garlic routing, which bundles multiple messages together for better traffic obfuscation. It uses its own internal DNS to access “eepsites”, not .onion addresses. As the digital environment evolves, so do the tactics employed by cybercriminals, law enforcement agencies, and privacy advocates.
While this isn’t an issue for most of the trip (since each relay only has access to the previous and next relays in the network), it is an issue with the exit node. Because of the relaying of data through the onion nodes, and the encrypting and decrypting taking place at each node, your internet connection will slow considerably. This means the Tor Browser is not recommended for streaming video, playing games, or downloading large files. This encryption and relaying of your browsing data prevents anyone who is watching from detecting which websites you are visiting. This makes it really appealing for those who want to avoid unnecessary surveillance or who need to communicate without fear of oppression or governmental retaliation. However, if you’re planning to spend any time exploring the dark web, it’s crucial you take the necessary precautions to keep your device, your data, and yourself safe.



