
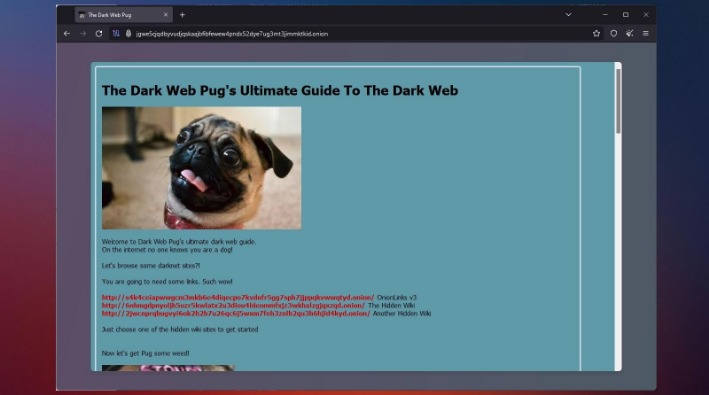
One of Daniel’s impressive features was the built-in functionality that showed whether a particular dark website is online. After more than a year of no updates, the site admin shut it down, reasoning that he couldn’t keep the list of onion links up-to-date. The Camouflage Mode is intended for people living in countries with heavy internet censorship, like China.
How Much Does It Cost To Use Tor Browser?

Also, you need to use a privacy-focused browser such as the Tor network to connect via nodes and proxy servers, which are more secure and aim to anonymize traffic requests. The Tor browser is able to access the special domain names, with the suffix .onion, used in the dark web. The dark web, which is what I’m discussing here, is a small subset of the deep web, and refers to websites that are specifically trying to stay out of sight. Another great source to find and explore dark web marketplaces or other sections is to visit Reddit’s resourceful forum. You can look for information on /r/deepweb, /r/TOR, or /r/onions, of which the latter is useful to find hidden wikis and more.
What Is A Cloud Access Security Broker?
NordVPN responded aggressively by upgrading its entire infrastructure to RAM-only servers and ending its reliance on rented servers. It also introduced a bug bounty program, hired a cybersecurity consulting firm to test its infrastructure, and then carried out a third-party security audit. You can use a VPN if you’re in a country that restricts or heavily monitors Tor usage. You can also use it if you don’t want your network administrator or ISP to be aware of your Tor usage. However, if you don’t fall into these categories, or are a high-risk internet user (e.g., an investigative journalist or whistleblower), combining a VPN with Tor might be unnecessary. This provider’s performance is top-tier, with full Tor Over VPN support to make things simpler.
Top 10 Best Dark Web Search Engines In 2025 Safe &
No standard web browsers can be used to access dark web content. Based on Firefox, the Tor Browser lets you surf the clear and dark web. All your traffic is automatically routed through the Tor Network. Ensure you download the Tor Browser from the official website to avoid downloading malware, spyware, or other viruses to your device. Following these practical tips will help you securely explore the Dark Web, reducing risks while protecting your privacy and digital security.

Step 3: Securely Connecting To The Network
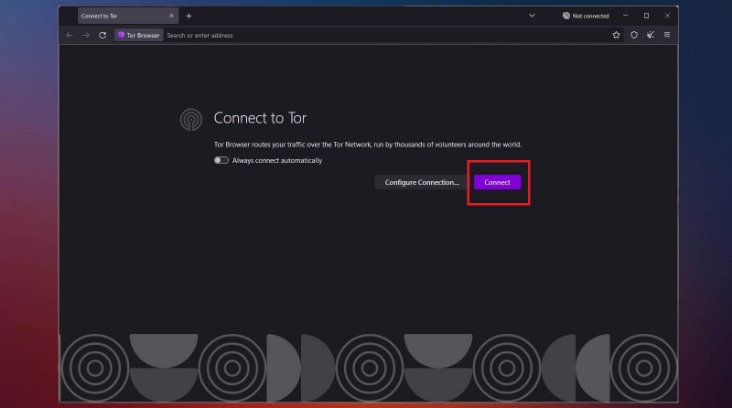
We strongly recommend researching your local laws to make sure it’s perfectly legal to use Tor and to only use it to access legal content. The correct top dark web browser download isn’t enough when it comes to safely accessing the dark web. It can access the regular internet through “outproxies,” but that’s not its strongest suit.
Is It Illegal To Enter The Dark Web?
Engaging in illegal activities—like buying drugs, trafficking stolen data, or distributing harmful content—is absolutely against the law. If you are looking to read combating crime on the dark web online, many resources and platforms are available that shed light on the ongoing efforts to curb the growing threats of cybercrime. Tor, designed by mathematician and computer scientist Roger Dingledine, along with two colleagues, emerged as an open-source project in the early 2000s. Other search engines like Haystak boast millions of indexed pages and advanced filtering options. However, none provide the same coverage or reliability as surface web search engines, so users often rely on forums, directories, and community recommendations to find trustworthy sites.
How To Access The Dark Web Using The Tor Browser
- Awazon became the successor of the popular AlphaBay market, which the authorities shut down successfully in July 2023.
- The area of the internet we access daily is known as the clear or surface web.
- Users must approach the Dark Web with caution and adhere to ethical practices, avoiding engagement with illegal activities or supporting harmful platforms.
- The Hidden Wiki is a popular onion link directory on the dark web offering categorized lists of sites.
- PIA doesn’t pull punches, so it strikes back against its competition with a proven-in-court no-logs policy, split tunneling, and even port forwarding to diversify its apps.
We’ll use the Tor browser for this guide, but any other browser that supports the Tor protocol will do. No matter what you do online, there’s always at least some risk of being tracked — especially on the dark web. While no method guarantees complete anonymity, you can minimize the chances of being tracked with the right precautions. As a general rule, it’s best to use the default settings in Tor or the Onion Browser. Changing any of the default settings can make websites misbehave or not load correctly. While Bitcoin and other cryptocurrencies provide some level of anonymity, blockchain analysis tools can trace illicit transactions.
JavaScript is a programming language used by websites to add interactive features, such as videos, forms, and dynamic content. However, on the dark web, JavaScript can also be exploited by hackers to track your activity or deliver malware to your device. To reduce the risk of these threats, it’s highly recommended to disable JavaScript when browsing dark web sites. Yes, governments and law enforcement agencies have developed sophisticated techniques to track and investigate illegal activities on the dark web. They can sometimes identify users through other methods, such as monitoring behavior, exploiting vulnerabilities or conducting undercover operations. For this reason, many people prefer to use a VPN to encrypt their connection to the Tor network, thereby preventing their ISP from being able to detect that they are accessing the dark web.
As your traffic passes through Tor, it’s encrypted and bounced between at least three relay points, known as nodes. This helps obscure the origin of the data (and makes it hard for anyone to find your IP address). But as a result, Tor Browser will feel much slower than a normal web browser. The Tor Project says that of the 2 million people using Tor every day, only 1.5% of them are accessing hidden or dark websites (that’s 30,000 people). Most dark web websites are in English; according to one estimate, a staggering 78% of information on the dark web is in English.
What Should I Avoid On The Dark Web?
People in countries with restricted internet access use the dark web to bypass government censorship and obtain unbiased news. In contrast, VPN over Tor setups won’t protect your real IP address if Tor leaks, require more technical setup, and aren’t supported by many VPN providers. Many transactions on the dark web use cryptocurrencies like Bitcoin for anonymity. Ensure you understand how to use cryptocurrency wallets securely, and never keep large amounts in a single wallet. Use a separate wallet for dark web transactions to further protect your funds.

Whether you’re a journalist, an activist, or simply curious, take the necessary precautions to remain secure. The hidden web (also known as the deep web or deep net) is the largest part of the internet. It comprises websites that aren’t easily accessible mainly because they are non-indexed, password-protected or paywalled. The dark web is a small subset of the deep web comprising purely non-indexed websites and services.
Tor’s anonymity has spurred many malicious actors to host dangerous sites on the network, including scams, phishing links, malware, and illegal content. The dark web isn’t just a hacker HQ or some deep-sea netherworld. It’s a corner of the internet where privacy is currency—and accessing it without protection? Whether you’re digging into whistleblower leaks, downloading files via secure .onion links, or just curious about what lives beyond the Google index, you need to lock in a VPN first.



