You can access the dark web on both Android and iOS, but their limitations make it less secure. The best Android option is the Tor Browser, available on Google Play. For added privacy, use Orbot, which enables system-wide Tor routing for other apps. IP2 is faster than Tor and offers stronger peer-to-peer security, as it uses one-way tunnels to encrypt traffic — meaning, only inbound or outbound traffic could be intercepted, not both. In addition, it uses a distributed network database which is harder to attack than Tor’s fixed, trusted Directory servers.
Best Practices For Accessing The Dark Web
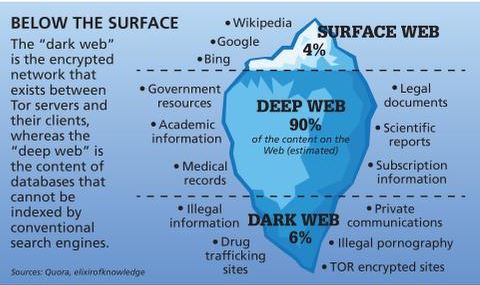
The deep web refers to anything that search engines can’t crawl.1 These pages aren’t public — not because they’re illegal, but because they require a login or special access. Think of your email inbox, banking dashboard, cloud documents, subscription content, or internal business tools. As the digital environment evolves, so do the tactics employed by cybercriminals, law enforcement agencies, and privacy advocates. Staying safe and anonymous often means continuously educating yourself, adapting your methods, and refining your tools. Ultimately, the Dark Web is neither purely nefarious nor inherently virtuous—it’s a dynamic environment shaped by the motivations and actions of its users. Your decisions, responsible conduct, and awareness of potential risks will determine your experience in this hidden realm.
Counterfeit Documents And Identity Kits
Install a mobile dark web browsing app — like Tor browser for Android or the Onion browser for iPhone — and enter an onion URL to start browsing. Dark web domains tend to be inconsistent — new ones pop up and others disappear, which makes sense if they offer questionable or illegal goods and services. Darren Guccione is the CEO and co-founder of Keeper Security, the world’s most popular password manager and secure digital vault. Keeper is the first and only password management application to be preloaded with mobile operators and device manufacturers including, AT&T, Orange, America Movil and HTC. Keeper has millions of consumer customers and the business solution protects thousands of organizations worldwide. Law enforcement agencies keep an ear to the ground on the dark web looking for stolen data from recent security breaches that might lead to a trail to the perpetrators.
Why Use Tor For Accessing The Dark Web?
It’s a good idea to connect to a trusted VPN before you even open the Tor Browser to access the dark web. Well, as long as you don’t visit sites with underaged models or that engage in human tracking or that sell drugs and other illegal items. That’s a trick question, because there isn’t even a good free VPN, much less a best VPN.
- The dark web has a reputation for being a lawless digital underworld filled with criminals and illicit activities.
- A VPN, in combination with Tor, further enhances the user’s security and anonymity.
- Users should exclusively download the Tor browser from the official torproject.org website to avoid potential security risks.
- Silk Road was one of the first dark web marketplaces and it allowed users to trade multiple types of nefarious goods and services, including weapons and identity fraud resources.
Steps To Install Tor
For government critics and other outspoken advocates, they may fear backlash if their real identities were discovered. For those who have endured harm at the hands of others, they may not want their attackers to discover their conversations about the event. If an activity is deemed illegal by the governing bodies you fall under, then it would be illegal. However, you can still take illegal actions within Tor that could incriminate you regardless of the browser’s legality.
Should You Use A VPN And Tor?
This is where an Onion website, like the Tor browser, comes in handy. It is the dark web’s version of Wikipedia with a massive links directory. You will find all the necessary .onion links to access any content or service on the dark web.
Check out my article for more information about the dark web and how to access it while staying safe. One way to stay safe is to use a VPN while accessing the dark web, so be sure to check out my article on the best VPNs for the dark web. Arguably, the best-known tool used to access the dark web is the Tor Browser.
FAQs About Navigating The Dark Web Safely
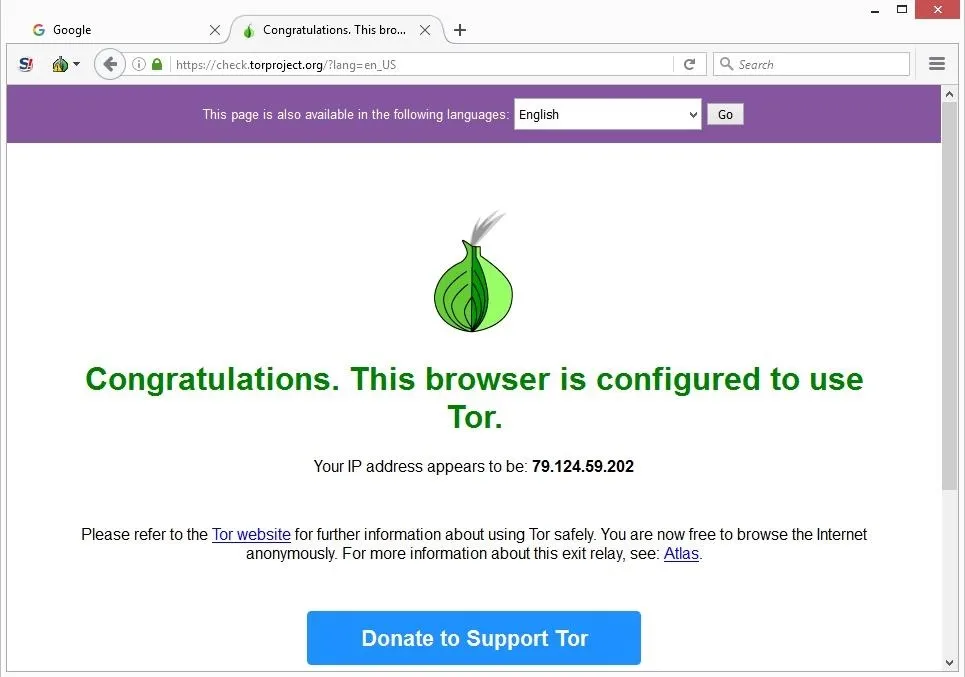
Accessing the dark web requires special tools and precautions, like using the Tor browser. However, the Tor network can be hacked, as evidenced by the 7 months of DDOS attacks experienced in 2022 (Securityaffairs)1. This requires your connection to go through multiple nodes and relays, which will slow down browsing on Tor.
The dark web also offers access to blocked resources in countries with strict government censorship on the internet. Citizens of such countries can use the dark web to bypass firewalls and access global information. The dark web exists to provide users with anonymity and privacy on the internet. Some users, such as whistleblowers or journalists working on sensitive issues in oppressive authoritarian governments, need privacy to carry out their activities. More seriously, free VPNs – particularly those offered as standalone services – sometimes make money by selling your data to third parties.
Best Practices For Staying Safe On The Dark Web
If you must download a file, verify its source and consider using a sandbox or virtual machine to open it safely, away from your primary operating system. The VPN encrypts your traffic before it enters the Tor network and all the way to its destination, so your traffic remains protected. This infects a user’s device and essentially blocks them out of it until they pay a “ransom,” usually in the form of cryptocurrency (so it’s harder to track and recover). Users could accidentally fall victim to ransomware just by clicking the wrong link or downloading a file on the dark web. If you’re in the U.S., you can make use of helpful tools like ExpressVPN’s Identity Defender to inform you if and when any of your data ends up on the dark web. This will allow you to take action right away and reduce the risk of any further damage to your data or identity.
Opinions expressed herein are those of the authors and not necessarily those of Analytics Insight, or any of its affiliates, officers or directors. The “VPN-over-Tor” approach offers added protection, even if Tor is compromised. By distributing communication over several nodes, it obscures the user’s IP address. Indeed, most nations; including the United States, the United Kingdom, and India, allow access to the dark web as a lawful activity. People often have bad feelings about the dark web, but not everything on it is illegal or dangerous.

What’s more, they can also sell you personal information on the dark web as your personal data has a monetary value on the dark web. The dark web is a playground for hackers, cybercriminals, and people with nefarious objectives. We strongly advise you against visiting it, even if your intentions are good. You can use these dark web investigation tools to check if your company’s data is available on the dark web. It offers outstanding privacy features and is currently available with three months extra free.
- This node decrypts your traffic and it reaches the destination i.e. the website you want to visit.
- It blocks trackers, prevents user fingerprinting, encrypts data, and reroutes your browsing so no one can see where in the world you are.
- This is because law enforcement often actively monitors these sites.
- Medical records, fee-based content, membership websites, and confidential corporate web pages are just a few examples of what makes up the deep web.
- In fact, journalists, privacy advocates and academics use it every day to protect their identities and get to material that has not been blocked.
By following these steps, you enter the Dark Web with more confidence and preparedness. Although it’s not inherently illegal to access the Dark Web, remember that certain sites and activities may be. Stay vigilant, trust your instincts, verify sources, and prioritize your security to make the most of the anonymity these networks provide. Even with Tor and onion routing in place though, you’re not suddenly completely invisible and free to do whatever you want, without repercussions. Certain details of your traffic can be intercepted at the entry and exit points of the node, by the people running those nodes, if they know what they’re doing and what they’re looking for.
Library Genesis offers a search engine for collections of books on such topics as computers, business, technology, and more. These are only a few of the .onion search engines that are available. While this doesn’t tell the exit node what your original IP address or your geographical location is, it could spy on your activity if the website you’re visiting isn’t a secured HTTPS website. But with the NSA setting up fake exit nodes, and growing concerns about the overall security of the network, you may need a VPN as well, if you want to ensure your privacy. Being hidden doesn’t translate into being completely protected from the possibility of tracking, or, when it comes to illegal activities, of risk.
Norton 360 Deluxe provides a comprehensive suite of protection that can help block malware and dangerous links in real time, and even detect scams using cutting-edge AI detection. Plus, it features a built-in VPN to encrypt your connection, hiding your IP address and online activity, for more anonymous and private browsing. However, because it’s almost completely anonymous, there are a lot of illegal images, information, products, and services on the dark web. Attempting to even view these can be illegal in many countries and states, so stay well clear of them if you want to keep a clean record and conscience. Once connected to Tor, you’re ready to begin exploring the dark web.



