You would also require a bitcoin wallet to store your bitcoins (or trade them later!). You can...
wpadmin
Layer a VPN (e.g., NordVPN) to mask your IP before entering darknet markets. A timeline of darknet...
The second category consists of data stores, which specialize in stolen information. Telegram channels supplement traditional onion...
As mentioned earlier, launching a cyberattack doesn’t require any hacking skills. Even people with zero technical knowledge...
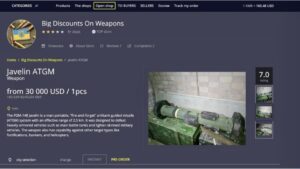
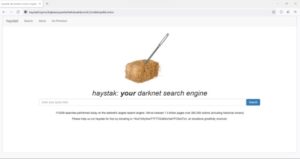
A verified list of darknet markets and services with links for educational reference. In Example 2, the...
Experience Flare for yourself and see why Flare is used by organization’s including federal law enforcement, Fortune...
The presentation sparked debate about whether the medical cannabis industry should be welcomed in Cassopolis. Warm the...
It benefits activists, whistleblowers, and journalists in highly monitored or censored contexts who communicate privately. Privacy-conscious people...
Even with Tor and a VPN, you’re not fully protected unless you also lock down your behavior....
Users should be well aware of these risks before venturing into this part of the internet. In...