A verified list of darknet markets and services with links for educational reference. In Example 2, the seller has put on a festive sale—201 American Express credit cards—with a special deal just in time for the holidays. All joking aside, cyber criminals will generate buzz and additional traffic by offering discounts like traditional advertising. As a new customer or dark market user, there are high chances you’re likely to get scammed. Therefore, research any Darknet markets with Tor, being careful to visit forums and check updated information to see if any sites have been flagged as suspicious or compromised.
How Can You Determine Where A Marketplace Is Located?
Introduced in September 2022, Torzon Hub is a darknet marketplace accessible via the Tor network, hosting more than 11,600 illicit items such as narcotics and cybersecurity tools. This platform boosts shopper trust by integrating vendor reviews backed by PGP verification. Torzon Hub provides a premium membership for enhanced perks and holds an estimated worth of $15 million, supporting transactions in Bitcoin (BTC) and Monero (XMR). Darknet markets have become a popular avenue for purchasing illicit substances, including LSD. If you’re interested in buying LSD from the darknet markets, it’s important to follow certain steps to ensure your safety and anonymity. Here’s a guide on how to buy from the darknet markets and purchase Avi LSD.

Paying For Your VPN
Officially, the Tor Browser is only available on Windows, Mac, Android, and Linux. Many experts advise against using third-party mobile browsers that utilize the Tor Network. As long as users take the necessary precautions, no one knows who anyone else is in the real world.

Commercial Services
If you’ve ever checked your medical results online through a portal that required a login, you were navigating the deep web. It’s huge, making up about 90% of the internet, but it’s mostly mundane, hidden behind login screens for privacy and security. Active for a decade since 2014, it is a widely used credit card shop used to source stolen credit card information such as dumps, CVVs, Wholesale Accounts. Security researchers have been monitoring forums within the cybercriminal underworld to investigate the leading markets operating in 2024. Never log in with your real name or reuse passwords from other accounts. Stick to cryptocurrency, avoid downloading anything, and don’t share any personal info.
How To Access Top Darknet Marketplaces Safely
Tails never writes anything to the computer’s hard drive, running only from the RAM of the computer, which is wiped clean when the computer is shut down. Check around with other users and ask if they know anything about the new marketplace. The “Hidden Wiki” (which can be accessed in a normal browser) offers a large collection of dark web links, but be careful, as many of those links are to dangerous websites. Naval Research Laboratory mathematicians and computer scientists in the mid-1990s.
Where To Find Darknet Market Links
If you get NordVPN, you can also use the Tor network whenever you want with its Onion over VPN servers. These are special servers from NordVPN that first hide your IP address and then route your traffic through the Tor network. The left-hand side features a column with different categories, as visible in the picture below. To stave off such attacks, they usually require users to solve complex problems to prove they’re not bots. The problems include identifying shapes or connecting different images. In repressive regimes, darknets play a vital role in enabling free speech and access to uncensored information.
Typical Use-Cases Of Dark-Web Marketplaces In 2025
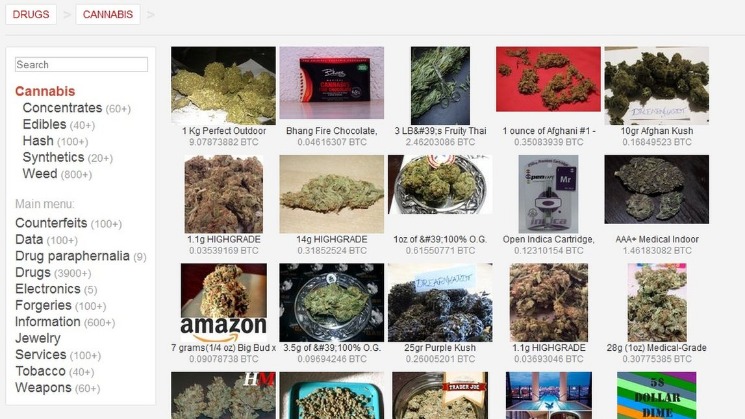
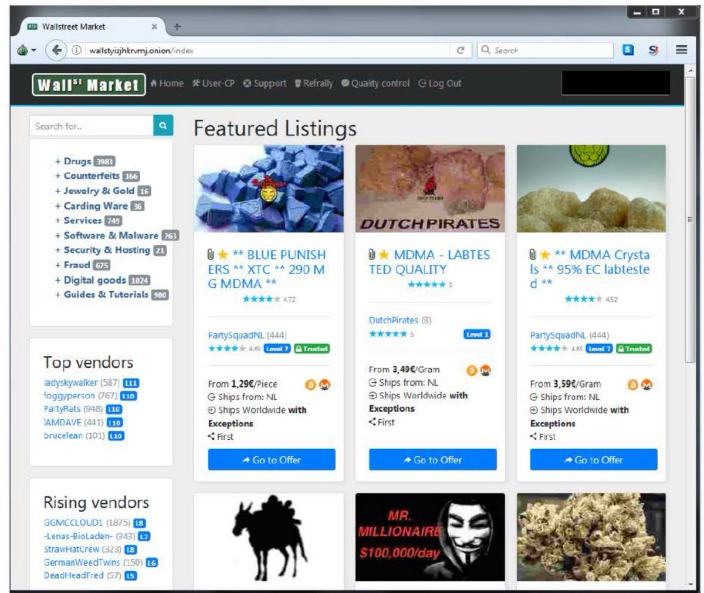
There are many different markets to choose from, each with its own unique selection of goods and services. Some popular darknet markets include Dream Market, Wall Street Market, and Empire Market. To create an account on a darknet market, you will typically need to provide an email address and a username. Some markets may also require you to provide additional information, such as a PIN code or a security question. Once you have created an account, you will be able to browse the market’s listings and make purchases.
Words Of Caution When Using Dark Web Sites
It’s been a constant back-and-forth between cybercriminals and law enforcement, with each new site trying to be smarter and more secure than the last. The second category consists of data stores, which specialize in stolen information. Today’s cybercriminals spread their activities across multiple platforms, making them harder to track and shut down. Do not click on any random links or download any files posted within anything as malware is very common on the dark web. If you have to email a message or files to a vendor, secure your communication with PGP (Pretty Good Privacy) encryption. This makes sure your messages are encrypted and only readable by the recipient.
- This means your ISP can’t see that you’re accessing the dark web (or indeed, the specific sites you’re accessing).
- Utilize search engines targeted to index links on the dark web like Torch or Grams__)); But keep in mind these search engines will also show up illegal content.
- Apart from the dark web markets that are operating online today, some raided platforms influenced many markets.
- There are multiple search engines on the dark web that can help you find what you’re looking for.
- In some countries, evading government restrictions to seek new political ideologies is punishable.
- The dark web has no shortage of criminal activity, scams, phishing sites, suspicious links, and malware designed to trick newbies.
Organizations need automated dark web monitoring to prevent cyberattacks. In 2022, for example, BidenCash was linked to the breach of over 1.2 million credit card records. One of the distinguishing features of Fresh Tools Market is its focus on providing up-to-date, freshly obtained tools and credentials.
However, the website has some security risks, and users experience glitches. Many listings involve stolen personal information, including credit card data, Social Security details, and full identity profiles. Dark web markets work much like regular e-commerce websites but with extra layers of anonymity and encryption. Buyers browse listings, place orders, and pay with cryptocurrency — typically Bitcoin or Monero — to obscure transaction trails. In this article, we’ll explore what dark web markets are, how they work, and why they’re so risky. We’ll also discuss examples of major marketplaces, myths about the dark web, and tips on staying safe in case your personal data ever ends up there.
Simply download the file, install the software, and you’re ready to use its web-based interface. Opennet connections are easier to use, but darknet connections provide more security against attackers on the network. The advantages of I2P are based on a much faster and more reliable network. Additionally, I2P doesn’t rely on hidden directories that serve as a resource for .onion domains. I2P can only be used to access hidden sites that are only available on the I2P network. But remember, it’s essential to take all the necessary and important security steps before entering such sites on the dark web.
Criminals use this information for money laundering, opening bank accounts, applying for loans, and draining your finances. Avoid downloading files, clicking on unfamiliar links, and sharing personal information. Additionally, do not attempt to buy anything on the dark web as most transactions are illegal and can lead to scams.
- Pastebins are text sharing services, useful for sending and sharing large snippets of code or text.
- In addition, we sampled ten darknet market products from each category and determined their price on the surface web (Table 9).
- The information you enter will appear in your e-mail message and is not retained by Tech Xplore in any form.
- Valued at approximately $15 million, Abacus Market is one of the most lucrative platforms in the dark web ecosystem.
- The dark web alert system is designed to urge you to take action before any significant harm is done.
Antivirus will ensure that any viruses or malware downloaded from the dark web are removed. The name of this dark web browser comes from the method it uses to encrypt messages. The Tor browser wraps data in different layers of encryption (like an onion) and sends it through a network of ”onion” routers. Each router the data passes through sheds away a layer of encryption and sends the partially decrypted message to the next destination. The process repeats until the message arrives at its intended destination. While this technique increases Tor’s security and keeps the dark web operations anonymous, it slows down the performance.