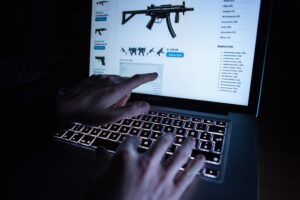
Credit card fraud checks also add latency to the transaction, severely slowing the checkout experience and leading to cart abandonment from legitimate users. Gift card cracking is a variation of carding where attackers use bots to systematically test large volumes of possible gift card codes on a merchant site in order to identify valid combinations. The stolen gift cards are then resold on the dark web or used to purchase goods, which are then resold for cash. Dark web monitoring is done with the aim of high ethics as well as intelligence gathering. Therefore, the organization should gather all the necessary info to guide them in identifying as well as tracking the exploits and the possible actions that cybercriminals take.
The Top Dark Web Hacker Forums In 2024
But relying on them exclusively to stop increasingly sophisticated attacks is proving ineffective. Bots also enable the carder to rapidly change the IP address from which they are attacking, which makes it much more difficult for traditional anti-fraud technologies to identify and block an attack. Moreover, it’s essential to provide the company staff with enough training as well as defined objectives of what they should look for to bolster the monitoring efforts. Perhaps that’s their option for generating consistent traffic and a steady influx of new members.
- After all, cybercriminals can use the cards to buy items, extract the cash from the account, or just continue to charge the card itself until the bank realizes that the transactions are fraudulent.
- This makes their crime less traceable by minimizing the number of transactions they need to make on the stolen card, making it easier for them to get away with it.
- While some users seek privacy, the ease of trading stolen data and illegal services remains a major cybersecurity concern.
- Post the dismantling of Joker’s Stash, cybercriminals displayed adaptability by establishing new marketplaces to fill the void, highlighting the resilience of criminal enterprises.
- The rise of contactless payments, especially during the COVID-19 pandemic, has significantly increased the volume of NFC transactions.
- In 2023, the dark web attracted an average of 2.7 million daily users, with Germany now leading as the country with the highest number of Tor users, surpassing the United States for the first time in years.
Top 7 Dark Web Marketplaces
- This gives security teams time to adjust their defenses before new techniques become widespread.
- In addition to new scams and schemes targeting online banking customers, we have seen the evolution of criminal marketplaces to trade in stolen information, stolen accounts, and stolen money.
- I’ve seen cases where security teams identified compromised card data from their institution appearing on the dark web weeks before they traced the actual breach point.
- Whether you’re a cybersecurity professional, researcher, or someone curious about the dark web, this article offers valuable insights into the forums shaping the cyber threat landscape today.
The rise of contactless payments, especially during the COVID-19 pandemic, has significantly increased the volume of NFC transactions. This growth has created more opportunities for fraudsters to exploit the technology. As the market for contactless payments continues to expand, so does the potential for NFC-related fraud. NFC is also used for identity verification, making it a target for identity theft. The app utilizes Host Card Emulation (HCE) to mimic a physical ISO NFC smart card by registering a service that extends HostApduService.
Helium Forum (Offline)
We’ll explore how credit card data is stolen, the workings of illicit marketplaces, and the processes criminals follow from acquiring data to converting it into profit. Additionally, we’ll discuss the risks users face when their financial information is compromised and provide actionable guidance on protecting yourself against becoming a victim. By shedding light on these hidden online networks, you will better understand the threats that exist in cyberspace and how proactive awareness can significantly reduce personal and collective risk. In2020, students at the Technical University of Darmstadt, Germany,developed NFCgate to capture, analyze, or alter NFC traffic. The “Ghost Tap” technique enablescybercriminals to cash out money from stolen credit cards linked tomobile payment services such as Google Pay or Apple Pay by relayingNFC traffic via NFC-enabled POS terminals.
Staying Protected: Tips For Individuals

When a card is verified as active, it can be used for purchases or resold in criminal networks. These attacks are fast-moving and difficult to trace, especially when businesses lack real-time fraud monitoring. Carders may also exploit weak verification systems, targeting e-commerce sites with poor fraud prevention measures in place. Unlike malware development/delivery and phishing, which are components of a larger attack chain, carding is the means and the end. This is because resellers of stolen card data are likely to pivot to other large-scale dump forums.
Dark Web Sources For Carding Data
Throughadvanced tooling and techniques, such as the “Ghost Tap”method and remote transaction relays, they can bypass detectionsystems and cause significant financial damage to victims. The globalnature of NFC payments and the anonymity provided by money mules andencrypted communication channels make these fraud operationschallenging to track and shut down. Typically,these merchants have a daily limit, so cybercriminals are alwayslooking for new ways to scale their operations by adding new moneymules who can open accounts for a commission. Traditional payments typically require some Cardholder Verification Method (CVM) such as PIN or signature.

Here, we delve into the various aspects of credit muling, shedding light on its risks and alternatives. One major hurdle for law enforcement is the jurisdictional limitations that come with combating cybercrime. Carders often operate across international boundaries, making it difficult to coordinate efforts and bring them to justice. Additionally, the ever-changing landscape of technology and the anonymity provided by the dark web further complicate the efforts of law enforcement agencies. Sentiment across this illicit criminal market – together with the continued departure or seizures of prominent vendors – indicates that this once-formidable enterprise is far from what it once was.
To overcome these challenges, Webz.io offers a stable and continuous flow of information from dark web forums and a tool to analyze that data. You can access deep and dark web data through our dark web API and perform detailed data analysis with Lunar. These tools help you easily investigate the illicit activities hidden in forums across the dark web. XSS is one of the most prominent and well-regarded hacker forums on the dark web. Named after the web security vulnerability “Cross-Site Scripting (XSS),” the forum caters primarily to Russian-speaking cybercriminals and hackers. It has gained a reputation for its professional approach and the high quality of its content, attracting a sophisticated and experienced user base.
Catch Crypto Criminals
You aren’t encouraged to buy carded items, carding tutorials, malware or basically anything that’s illegal in any way whatsoever. If you wish to learn carding, share your experiences, talk to carders, or just buy tools of the trade, I’m confident these will get you exactly that. Learn how to automate financial risk reports using AI and news data with this guide for product managers, featuring tools from Webz.io and OpenAI. Users share information about vulnerabilities and exploits, enabling others to capitalize on these weaknesses before they are patched.
“No Place In Our Networks”: FCC Hangs Up On Thousands Of Voice Operators In Robocall War
In today’s increasingly digital economy, the underground trade of stolen credit card information is thriving, fueled primarily by anonymous marketplaces on the dark web. Understanding how this shadow economy operates is crucial—not only for law enforcement and cybersecurity professionals but also for everyday individuals whose personal and financial information is at risk. Carding forums themselves serve as essential tools for cybercriminals, providing a platform for exchanging knowledge, sharing techniques, and trading stolen information. These forums offer a wealth of resources, ranging from tutorials on carding techniques to marketplaces for buying and selling stolen credit card data.

Operating on both the dark web and the surface web, Exploit.in serves as a hub for malicious actors seeking to buy and sell exploits, malware, and stolen data. The forum is notorious for its role in facilitating unauthorized access to networks and distributing malware. FreeHacks, a Russian-based forum, is one of the largest hacking communities in the world.
They also suggested that vendors are adding invalid data to increase the size of their database. Until now, carding was seen as a way for novice crooks to begin their criminal careers because of the low startup capital required. It’s always been fairly cheap to buy a few valid payment card details, monetize them, and make a small profit from these low-effort endeavors. This makes sense—those just starting out in the business haven’t earned the illicit funds they’ll need to invest in more expensive material that can make them even more money in the future. If it’s too expensive to start out, this is a huge, and often insurmountable, barrier to entry. Carding has always been seen as a gateway to the more involved and nuanced types of cybercrime.