These features help establish trust between buyers and sellers, providing users with a sense of security that many other markets lack. As cyber threats grow more sophisticated, organizations are keeping a close watch on the dark web. Companies use dark web monitoring to scan for leaked data, stolen credentials and breach indicators, helping them track and identify perpetrators. But let’s be realistic, the best defence isn’t just playing detective after the fact.

How Accessible Is This Website?
Perhaps, the lack of rules and anonymity of the dark web can be tempting, but those are the same things that make it a risky environment. Moreover, it’s not only the entertainment industry that gets hit; some sell cracked versions of the most expensive software, and others offer pirated eBooks and academic material at cheap prices. With all of that in mind, you need to tread carefully when browsing, in terms of the sites you visit and the other users you interact with. Bear in mind too that laws about freedom of speech and censorship vary from country to country, which is part of the reason the dark web exists in the first place. DuckDuckGo is the default search engine inside the Tor browser, and once you turn on the Onionize toggle switch in the search box, you’re able to use it to find dark web links.
Ignoring these risks can lead to financial losses, reputational damage, and regulatory penalties. A high degree of security measures further safeguards users on dark web marketplaces. Buyers and sellers alike use encryption tools, fake identities, and VPNs to add extra layers of protection.

Dark Web Phishing Kits: How Hackers Sell Ready-Made Scams

Silk Road, operational from 2011 until its shutdown by the FBI in 2013, demonstrated the scale of these marketplaces, with thousands of users worldwide. Other marketplaces, like AlphaBay and Dream Market, have since emerged, only to face similar fates of law enforcement crackdowns. Despite these closures, new platforms continuously rise, adopting advanced security measures to evade detection.
Dark Web Search Engine
Another private cryptocurrency you’ll find being used is Monero, which prides itself on being untraceable. Even with Tor and onion routing in place though, you’re not suddenly completely invisible and free to do whatever you want, without repercussions. Certain details of your traffic can be intercepted at the entry and exit points of the node, by the people running those nodes, if they know what they’re doing and what they’re looking for. You’re also open to threats like end-to-end correlation attacks, so while Tor is a lot more secure and private, it’s by no means completely safe. Whatever the outcome of the CyberBunker trial, the operation against Xennt has provided police with an Aladdin’s cave of information on other criminal activity. One of the German officers charged with analyzing the contents of the CyberBunker servers told me that the volume of data was unwieldy, but its content fascinating.
Keeper has millions of consumer customers and the business solution protects thousands of organizations worldwide. Ransomware-as-a-service (RaaS) kits have been available on the dark web for several years, but those offerings have become far more dangerous with the rise of specialized criminal groups like REvil or GandCrab. These groups develop their own sophisticated malware, sometimes combined with pre-existing tools, and distribute them through “affiliates”. Medical records, fee-based content, membership websites, and confidential corporate web pages are just a few examples of what makes up the deep web. Estimates place the size of the deep web at between 96% and 99% of the internet.
Escrow Services
These sites often look basic or outdated, and their URLs are lengthy strings of random letters and numbers. Keep in mind that visiting the dark web isn’t illegal, but engaging in criminal activity there is. Even after Silk Road went down, dark web marketplaces haven’t slowed down.
Leverage Free Cybersecurity Resources
- I’ve used it; shipping’s discreet—plain packages or DeadDrops—and uptime’s been flawless, rivaling Abacus.
- Criminals use this information for money laundering, opening bank accounts, applying for loans, and draining your finances.
- From drug sales and breached data to scam services and malware, dark web markets are some of the most dangerous corners of the internet.
- Under U.S. federal law (18 U.S. Code 472), possession or use of counterfeit currency can result in up to 20 years in prison.
- The police referred to him only as Julian K. Shortly after Julian K.’s arrest, DarkMarket was shuttered by the German police.
- The layers of encryption hide your data and activity from snooping eyes.
While there are other browsers you can use to get on the dark web, Tor is usually recommended as the best for most people in terms of the features it offers and the ease with which anyone can make use of it. To get on the dark web, you need a browser built for the job, and the best in the business is Tor. Tor is a browser engineered for extra security and privacy, and can be used to navigate the normal, surface web as well as the dark web. It blocks trackers, prevents user fingerprinting, encrypts data, and reroutes your browsing so no one can see where in the world you are. DarkMarket also advertised itself as being the only such site administered exclusively by women. This was an intriguing boast—a prosecutor told me it was made to gain users’ trust—but it was untrue.

What Is The Black Market?

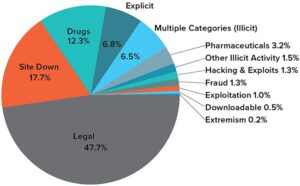
Active for a decade since 2014, it is a widely used credit card shop used to source stolen credit card information such as dumps, CVVs, Wholesale Accounts. It’s been a constant back-and-forth between cybercriminals and law enforcement, with each new site trying to be smarter and more secure than the last. In 2019, there were approximately 8,400 active sites on the dark web, selling thousands of products and services daily. As of 2020, nearly 57% of the dark web was estimated to contain illegal content, including violence and extremist platforms. Today’s cybercriminals spread their activities across multiple platforms, making them harder to track and shut down.
Unmasking The Dark Web Economy: Key Hubs And Cybersecurity Implications
If you ever have to connect to public Wi-Fi, make sure to use a VPN to keep your browsing safe and private. According to a recent trend, the dark marketplaces faced a decline in revenue. Chainanalysis, a blockchain analysis firm, conducted research that shows that the revenue decreased from $3.1 billion (2021) to $2 billion (2024). On the dark web, you don’t need to be a technical expert to design ransomware, and that’s dangerous. Even people with little to no knowledge can buy ready-made ransomware and launch attacks on their victims. If for any reason, you decide to visit these hidden corners of the web, ensure you at least study and understand the common traps.

Hidden services can operate while keeping the physical location of the server hidden, which makes tracking and shutting them down considerably more challenging. By consistently applying these straightforward security tips, you can significantly mitigate risks and better protect your privacy, finances, and legal standing when interacting with dark-web marketplaces. Understanding both the lawful and unlawful scenarios helps provide a balanced view of their practical applications in 2025. Overall, Abacus Market distinguishes itself through rigorous security measures, effective moderation policies, and a strong emphasis on protecting user privacy. Despite minor accessibility inconveniences, these strengths have solidified its position among the top dark-web marketplaces in 2025. An intuitive, user-friendly interface is crucial, especially given the complex nature of dark-web interactions.
Popular Dark Web Marketplaces Of Today – Detailed List
Mega Market is a new yet popular shop on the dark web that reached a skyrocketing reputation after the closure of the Hydra market. It allows you to buy and sell a wide range of products and services with a good user experience. This site supports PGP encryption and two-factor authentication features. To prevent the users from DDoS attacks, it provides personal marketplace domains to high-volume buyers and sellers.