
However, it also supports legitimate uses like protecting free speech and accessing information in censored regions. You can buy credit card numbers, all manner of drugs, guns, counterfeit money, stolen subscription credentials, hacked Netflix accounts and software that helps you break into other people’s computers. Buy login credentials to a $50,000 Bank of America account, counterfeit $20 bills, prepaid debit cards, or a “lifetime” Netflix premium account. The deep web is just the part of the internet you can’t find with a search engine. It’s not mysterious or spooky; it’s home to everyday things like scientific research, medical records, private financial information, and secure communications. The dark web is neither entirely a haven for illicit activities nor a utopian space of limitless freedom.
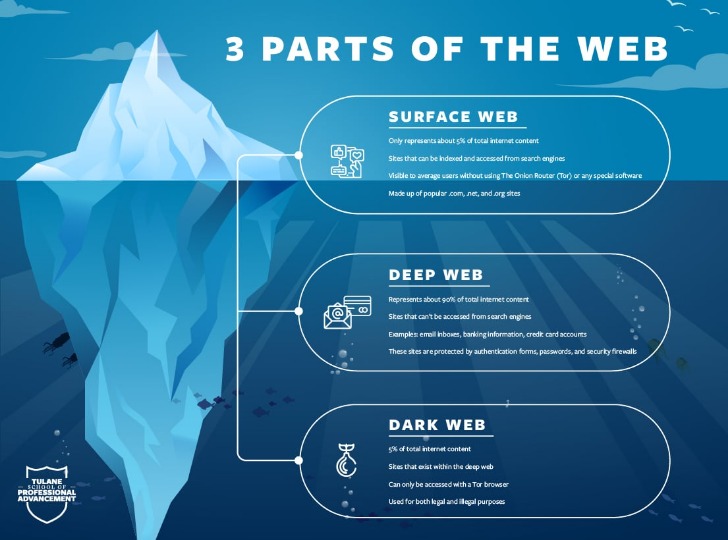
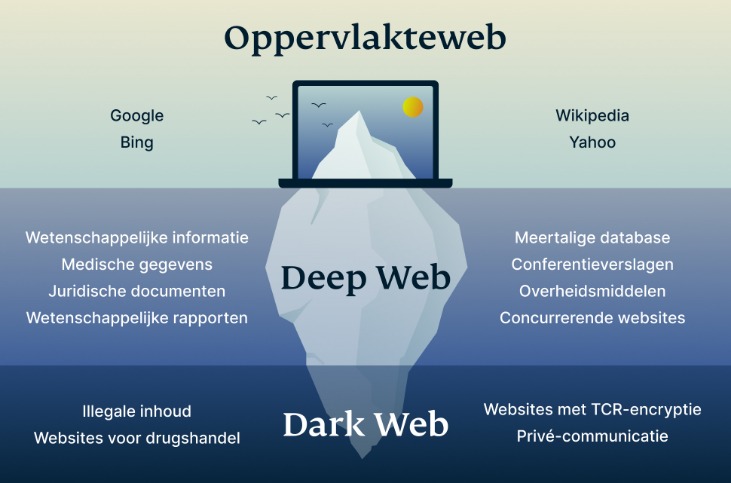
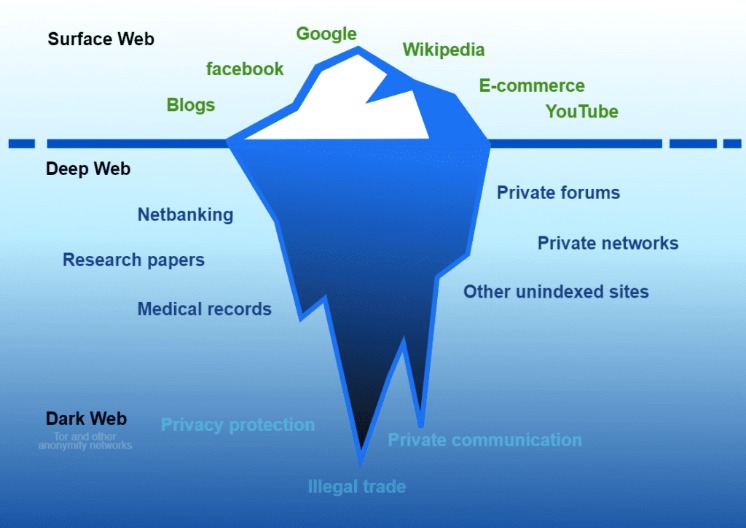
The deep web is made up of content that search engines such as Google do not index. Such data includes medical records, financial information, research papers, private forums and networks, and other content. But accessing the Dark Web is not just about downloading and installing the Tor Browser. Users must also navigate through .onion websites—domains that are specifically set up for use within the Tor network. These websites do not appear in traditional search engines, and their addresses are often a string of seemingly random letters and numbers.
Understand Legal Risks
Some of these are well-known, established threats that circulate in this nook of the web. However, others may be taking advantage of the dark web’s reputation to trick users out of large sums of money. Also, some users on the dark web may attempt phishing scams to steal your identity or personal information for extortion.
Charging the operators with a long grocery list of crimes ranging stolen data, drugs, and malware. These things do happen on the dark web, but they are one piece of the jigsaw. Once information has been exposed on the dark web, removing it can be extremely difficult. Unlike the surface web, there is no centralized authority or search engine to request takedowns from. Information often gets distributed across different forums, marketplaces and networks, making it nearly impossible to track. The dark web is rife with scams, from fake product listings to phishing schemes that steal personal data.
IV Verifying The Authenticity Of Links And Resources
The advantages of I2P are based on a much faster and more reliable network. Additionally, I2P doesn’t rely on hidden directories that serve as a resource for .onion domains. I2P can only be used to access hidden sites that are only available on the I2P network. As I mentioned previously, the dark web is quite popular with journalists, political bloggers and news publishers, and others who run the risk of imprisonment in countries like Iran and others. Supreme Court will allow the FBI to search and seize any computer that’s using the Tor browser or VPN. Rule No.41 allows a federal judge to issue a search and seize warrant for any person who is using anonymity software like Tor.
Verified Social Channels And News Sites
- The dark web is a part of the internet that you only step into with a specific tool (Tor, more on this later in the article).
- Yes, people have been arrested for certain activities on the dark web.
- In some countries, exploring new political ideologies can be considered an imprisonable offense, and those who visit restricted websites could be placed on a watchlist or targeted for jail sentences.
- If you have any questions or suggestions regarding the accessibility of this site, please contact us.
For businesses, proactive measures, including regular cybersecurity risk assessments and dark web monitoring, are vital to safeguarding sensitive information. Accessing the dark web presents significant risks and challenges, even for well-informed users. While it offers anonymity and privacy, these benefits come with considerable dangers, including exposure to illegal content, cybersecurity threats, and potential legal consequences. The dark web represents a much smaller segment of the deep web, accessible only through specialized tools like the Tor browser. Unlike the deep web, which hosts primarily lawful content, the dark web is notorious for enabling anonymous activities, including illegal trade and the sale of stolen data.
Our Network
- SecureDrop is a dark web link that allows whistleblowers on the dark web to communicate and share information with journalists safely and without being tracked.
- In 2021, some of the most popular marketplaces included Dark0de, Torrez, and OpenRoad.
- However, they also play an important role in how these groups orchestrate and monetize their attacks.
- The dark web, being a hub for criminal activities like identity theft and malware distribution, exposes you to various security threats like malware or phishing.
- You should be aware that law enforcement agencies may be monitoring the dark web and that visiting certain websites or engaging in illegal activities can result in criminal charges.
- Malware, ransomware, and hacking tools are also readily available for purchase or rent, enabling attackers to launch sophisticated campaigns.
You are not required to provide your personal information to create an account. The email service is available both on the surface and on the dark web. The goal of an anonymous and privacy network, Tor, is not to engage in the extensive collection of data. However, data is required for understanding, monitoring, and improving the network. Furthermore, data will help to detect attacks against the network and possible censorship events. Even without monitoring your browsing activities, DuckDuckGo will offer decent answers to your questions.
What Is The Dark Web? Myths, Realities And Cybersecurity Risks
Some markets are relatively short-lived (thanks to law enforcement), but others are notorious enough that they survive, for instance, Silk Road, AlphaBay, and Hansa. The dark web isn’t just one sketchy marketplace hiding in a corner of the internet; it’s more like a messy, unregulated community with everything from freedom fighters to full-blown cybercriminals. Use it to link your GitHub account, Twitter, Bitcoin address, and Facebook. This .onion link makes it impossible for hackers to impersonate your profile. Your data is encrypted in the Tor browser before reaching the ZeroBin servers.
Take Extra Security Precautions
Because, as our cybersecurity experts have validated through decades of research and practice, your data has a price. In one of the most famous examples, the FBI took down Silk Road, one of the largest illegal marketplaces to ever exist. Its founder, Ross Ulbricht, was imprisoned for 10 years before being pardoned by the US government. The dark web isn’t automatically a dangerous place, but it’s not risk-free. Like any tool, it depends on how you use it — and how careful you are when using it.

Also, some toxic chemicals are peddled on the dark web that may cause severe damage to the targets. For your optimum dark web safety, you should ensure that once you’re done browsing the Darknet, shut all the browser windows as well as any other content that could be connected. NordVPN has a strict no-logs policy to ensure user privacy and employs 256-bit AES encryption. It is also available on various operating systems, including Linux, Windows, MacOS, iOS, and Android. However, it’s important to note that NordVPN can see your traffic details before encrypting them, even though it does not keep logs. A VPN helps you browse the web more securely and privately by adding an extra layer of encryption to your data.

In due course, the framework was remodeled and made public as a secure browser. There are often copious amounts of how-to articles, software exploits, and hacked credentials for sale. Not every visitor is a criminal, but this is where most cybercrimes begin. No user names are tied to actual identities, and no moderation like one may find on Reddit. Users leverage these platforms to organize protests, whistleblow, share survival guides, or share files P2P.
Exploring The Dark Web: Understanding Its Role In Cybersecurity Threats

These sites are built for privacy and anonymity, and Google’s web crawlers (also known as “spiders” or “bots”), which look for websites to index, can’t access or “crawl” these hidden sites. Most links are accurate and still active, and each one includes a short description that’s usually spot-on. It’s a solid starting point for exploring, but it’s important to read descriptions carefully — some links lead to illegal or dangerous content. The dark web isn’t illegal in most places, but using the Tor browser can be. This special browser helps protect your privacy by masking your identity and hiding your online activity. For example we have a ‘staging’ version of this very website that is blocked from being indexed by search engines, so we can check stories before we set them live.
The accessibility of it for potential criminal activities has also been reported, even though some people use it to avoid government censorship. The Dark Web is a component of the internet that is not indexed by traditional search engines and requires special software to access. It’s where illegal activities occur and is home to some of the most dangerous elements of the online world. At the same time, these networks can also facilitate exploitation, hate speech, and other harmful activities. Laws pertaining to anonymity and the use of privacy-enhancing tools vary widely from one country to another.



