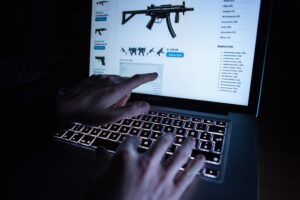
However, if you go poking around in illegal sites and services or don’t practice good operational security by offering up personal information or trying to perform illegal activities, it very much isn’t safe. You may be targeted by law enforcement, exploited by hackers, or threatened by criminals using the dark web for nefarious purposes. Because of the range of goods and services found for sale and the conversations that occur around these sales, dark web marketplaces can be precious sources of data on criminal activity. As such, they are normally under intense scrutiny from law enforcement and security professionals alike. A dark web search engine like DuckDuckGo offers impressive anonymity features and makes it easy to access the shops. These search engines neither track your search queries nor record any information, improving digital privacy and keeping your data private.
Dark Web Black Market Technologies And Tools
- Cybercriminals go on dark web marketplaces to buy and sell illicit goods and services.
- But remember, it’s essential to take all the necessary and important security steps before entering such sites on the dark web.
- Dark web markets work much like regular e-commerce websites but with extra layers of anonymity and encryption.
- One of the biggest problems cybersecurity teams face isn’t a lack of tools — it’s too many alerts.
- Platforms known for consistently resolving issues and eliminating fraudulent vendors quickly gain credibility and user loyalty.
Tor Links is a backup directory of “.onion” sites in case other directories go offline. The best Tor sites are under constant threat of closure, including Tor directories like the Hidden Wiki, so having a backup in case one goes down is handy. ProPublica is a non-profit, Pulitzer Prize-winning news outlet that focuses on abuses of power and issues of public trust. ProPublica’s investigative journalism can upset powerful interests, so the outlet joined the dark web to help their journalists and readers access their content anonymously. Being on the dark web also lets whistleblowers send material to ProPublica without fear of reprisal. If the VPN connection fails, the automatic kill switch will kick in, temporarily breaking your traffic.

Dark Web Monitoring Solutions: Detecting Threats Before They Happen
Even if a market has strong encryption and escrow, its operators could vanish. Recent examples include Yellow Brick Market (exit-scam January 2021) and BigBlue Market (April 2021). Always withdraw your funds rather than leaving them in a market’s wallet. Track and analyze darknet activities using our advanced cyber threat intelligence platform to stay ahead of emerging threats. The Dark Web refers specifically to websites and services hosted inside Darknets.

Author & Researcher Services
- Additionally, clients, unsure of the firm’s ability to secure their data, began terminating contracts, resulting in a 20% revenue loss over six months.
- I2P, or the Invisible Internet Project, allows you to access the ordinary and dark web.
- “A lot of people use it in countries where there’s eavesdropping or where internet access is criminalized,” Tiquet said.
- To get on the dark web, you need a browser built for the job, and the best in the business is Tor.
- As a user or cybersecurity professional, approaching these marketplaces demands utmost caution, thorough knowledge of operational security, and constant awareness of legal boundaries.
Cyber threat intelligence (CTI) helps organizations predict, understand, and defend against cyber threats, enabling proactive protection and reducing the impact of attacks. Darknets are not limited to criminal activities; nation-state actors use these hidden platforms for espionage, disseminating propaganda, and recruiting agents. The significance lies in the potential compromise of national security.
Individually, they are able to yield significant high incomes compared to other types of sellers. Manual monitoring of the dark web is inefficient and risky due to the sheer volume of data involved. Organizations need automated dark web monitoring to prevent cyberattacks. This platform has rapidly become a key player in the fraud market, trading in PII and SSH credentials while making use of both the clear and dark web.
The Dark Web And How To Access It
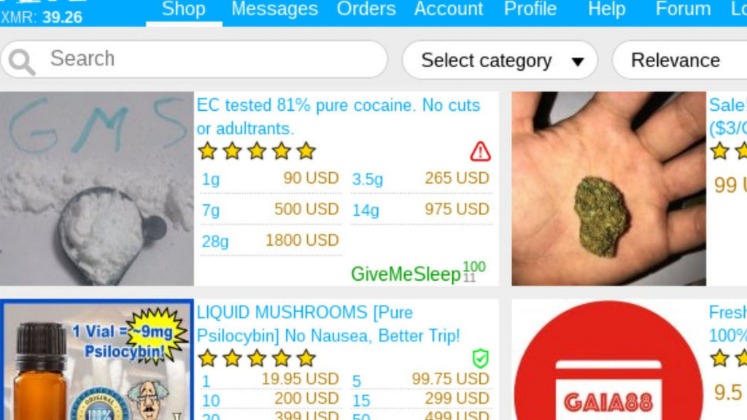
Finding a trusted dark web marketplace can be difficult, but we offer everything users need for a safe and smooth experience. The key differences between dark web markets and regular online stores are clear. Regular stores are public, with visible ads and a standard payment process. They usually accept cryptocurrencies, such as Bitcoin, which keeps transactions secret. There are no visible ads or trackers, and the design is often very simple.
Is Using The Tor Network Illegal?
But, perhaps a big surprise to anyone thinking the Dark Web is just for criminal activity, it can also be leveraged for legitimate purposes. In many places, including the U.S., the UK, and the EU, accessing the dark web is legal for legitimate purposes. However, many sites on the dark web host illegal content or activities, and engaging with those can lead to serious legal consequences.
Words Of Caution When Using Dark Web Sites
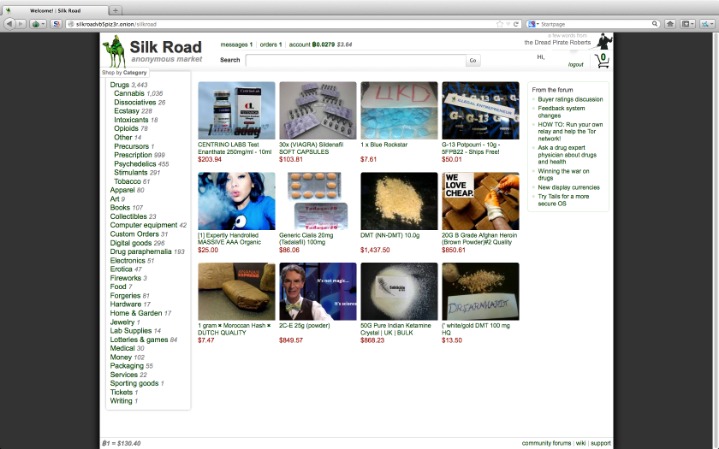
The dark web addresses are a randomly-scrambled sequence that generates URLs, mostly hard to remember ones. For example, the URL of Silk Road is rather unintelligible and may look something like “gan4arvj452janndj4a76.onion”. For example, you can only find your Facebook friends, photos, and other information by logging into your Facebook account and finding the information there. On the deep web, you can find such “private” information on web pages. So, that means that the number of pages increased by over 100 trillion in just over three years.
A VPN hides your internet activity, making it harder for your connection requests to be traced back to you. It’s a precaution to protect yourself before diving into the dark web. For recommendations on choosing a VPN, look for expert reviews and articles. The Dark.Exchange Application Programming Interface (API) provides programmatic access to Dark.commodity content and evidence based statistics. Our Dark.Ticker schema was designed to easily integrate with leading threat intelligence platforms for maximum scalability. It offers outstanding privacy features and there is currently a discounted rate available through this link.


You need to register first to purchase products from this marketplace. Bohemia is a modern dark web marketplace with a great user interface that is easy to use and navigate. It asks you to pay the merchant fee if you want to sell something, preventing the buyers from getting scammed. World Market is another largest dark web shops that deals with various goods and services.
Accessing it requires special software, such as the Tor browser, which provides anonymity by routing your connection through multiple servers. The black market, with its myriad links and hidden pathways, doesn’t have to be a forbidden zone. With the right tools, like Forest VPN, and a little know-how, it can be explored safely and legally. Whether you’re on a quest for rare information or simply curious about the unseen layers of the internet, the journey is yours to take, and Forest VPN is your trusty guide. Since the dark web isn’t indexed by standard search engines, sites like Ahmia act as modified directories to help users discover onion sites.
Onion Links: How To Access Them
The Darknet is a subset of the Internet operating over encrypted, anonymous overlay networks that require special software like Tor, Freenet, or I2P. You’re only scratching the surface when you use the Internet for daily activities—reading news, managing finances, running businesses. Search engines like Google, Bing, and Yahoo can access just about 4% of the web.

To safeguard sensitive information, businesses must adopt comprehensive cybersecurity strategies, including regular risk assessments, security gap analyses, and the deployment of tools like dark web monitoring. These measures not only help identify vulnerabilities but also enable swift action to mitigate threats before they escalate. Investing in robust cybersecurity solutions tailored to your organization’s needs is no longer optional; it is essential to ensure operational continuity and maintain stakeholder trust.