The deep web rests below the surface and accounts for approximately 90% of all websites. This would be the part of an iceberg beneath the water, much larger than the surface web. In fact, this hidden web is so large that it’s impossible to discover exactly how many pages or websites are active at any one time. If we continue to visualize the entire web like an iceberg, the open web would be the top portion that’s above the water. From a statistical standpoint, this collective of websites and data makes up under 5% of the total internet.
So, we know accessing the dark web is legal and provides many benefits to well-meaning users, such as enhanced privacy and defying censorship. Not only does Tor’s encryption system keep your activity anonymous, it keeps host websites hidden too. You can see why this ecosystem would be so attractive to those involved in criminal activity. The dark web lives on the Tor ecosystem and can only be accessed through the Tor browser.
Stay In Touch With Us
These onion addresses will remain online even if the original page disappears. It also keeps the graphical copy and text of the page for better accuracy. Using the ProtonMail .onion site offers security and privacy advantages. Moreover, the company also uses HTTPS and SSL encryption on the Onion site for extra protection.
Home To Illicit Activity
The size of the Deep Web surpasses the Surface Web while remaining secure as an Internet zone. Almost 90% of all the websites are on Deep Web and are majorly used by Government agencies, corporations amongst others. These websites are protected behind the security walls, authentication form and password. Almost any type of illegal and legally questionable products and services can be found somewhere in the internet’s underground. Furthermore, the global nature of the Dark Web presents jurisdictional hurdles and legal complexities.

Hacking Services And Data Breaches
In these cases, the law may treat temporary, browser-facilitated possession as a crime because the visit leads to the computer holding contraband material. For the open web, just type your name into Google and see what comes up. Whether this is a Linkedin profile, Facebook, social media, or any community involvement, chances are that you already have some online presence. As most malware is designed for Windows, another way to stay safe is to switch to a different operating system.
For maximum security users should only access sites with the .onion suffix via the browser. Knowing where online materials are – and who is searching for them – makes it possible for search engines like Google to sell advertisements. This accounts for well over 80 percent of the company’s revenue, linking people who are searching with the millions of sites out there that pay Google to list their content. SentinelOne’s Singularity Endpoint continuously monitors system activities, file changes, and other critical processes to protect against malware and dark web security threats.

A Quick Guide On How To Use A VPN With Tor
The Hidden Wiki is a longstanding directory of dark web sites that offers a way to browse onion services. It’s been around for many years and helps users navigate the dark web by curating links to various resources. Note that Hidden Wiki links sometimes lead to unsafe content, so be wary about what you click. Use your common sense to steer clear of online scams and illegal activity. A dark web browser, like the Tor browser, is designed to access hidden networks. It routes traffic through several encrypted nodes, concealing user identity and location.
A Dark Web Search Engine
This technology was instrumental in dismantling the Welcome to Video platform, a dark web site distributing child pornography, where investigators traced payments to arrest over 300 suspects worldwide. Accessing the dark web is not inherently illegal in many jurisdictions. It is a part of the internet that requires specific software, such as Tor, to access.
Legitimate Uses Of The Dark Web
The deep web is like an archive, containing an unsorted pile of websites and resources that are largely inaccessible to normal users. The Dark Web is said to be 5,000 times bigger than the surface web, and yet, it cannot be accessed through a normal browser or a search engine. In short, the Dark Web definition is based on the idea of an encrypted network that can only be accessed with the help of certain software. The dark web is a domain that provides anonymity to site owners and guests so they cannot be monitored by outsiders. Although many people use the two terms interchangeably, they are two different layers of the internet.
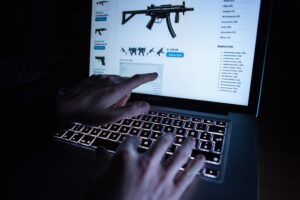
The availability of weapons and firearms on the Dark Web offers a concerning avenue for criminals and individuals with malicious intent. Underground arms dealers utilize the anonymity and encryption provided by the Dark Web to offer a variety of firearms, ammunition, and related accessories. In the next sections, we will uncover the hidden dangers of the Dark Web and the measures taken by law enforcement agencies to confront these threats. Ulbricht was convicted on multiple charges, including conspiracy to commit money laundering, conspiracy to commit computer hacking, and conspiracy to traffic narcotics. He was sentenced to life in prison without the possibility of parole, serving as a stark warning to those who sought to operate illegal marketplaces on the Dark Web.
While in theory you can buy legitimate products and services on the dark web, remember that anonymity works both ways. If you pay for something and it never arrives, you may well not be able to track down the seller to get your money back. A reference to how Tor works; sending encrypted traffic through layers of relays around the globe as it hides content, the sender, and their location. Users need a special browser with added software to access the tor dark web in the first place. There are also millions of servers which only store data which can’t be accessed via a public web page.

A wide range of illegal activities take place through the dark web, such as Internet sex crimes, illegal drug dealing, and other criminal activities. However, not all of the activities that take place on the dark web are illegal. The dark web is full of normal chat rooms and can also be a safe and anonymous place for a journalist to break a story. The dark web is similar to the Internet, which people normally use on a day-to-day basis. Such networks use the Internet to operate but require certain software or other avenues to access it.
- When you create a free Proton account, you get encrypted email with 1 GB storage, two password vaults, and one VPN connection.
- Many people install a VPN as well, but then you’re putting your trust in an additional third party to not track your activities or report them to anyone else.
- Hence, you never know when a popular .onion site is going to vanish, or even die.
- Designed to be hidden from conventional search engines like Google or Bing, the dark web is a portion of the internet.
- The dark web, through some specified browsers, allows users to circumvent censorship.
- IBM Security X-Force, for example, reported that 29% of its ransomware engagements in 2020 involved REvil.
“Darkweb Research: Past, Present, And Future Trends And Mapping To Cyber Threats”
Dark web marketplaces are websites where you can exchange illicit goods and services like stolen credit cards, account login credentials, counterfeit items, drugs, and other items. Usually dark web transactions are made with Bitcoin or other cryptocurrencies. A 2014 study found that the most common type of content found on Tor, the most popular darknet, was child sexual abuse material. The term ‘deep web’ doesn’t mean anything nefarious – it’s estimated to make up about 99% of the entire web. It refers to the unindexed web databases and other content that search engines can’t crawl through and catalog.

Cybersecurity experts often use the dark web to stay ahead of cyber threats. By monitoring marketplaces and forums, they can gather critical information about vulnerabilities, data leaks, and the tools hackers use. This helps them anticipate potential cyberattacks and better protect organizations and individuals.