All of this is intolerable when you consider there are simple alternatives that let you own your data and give you the freedom to make your own online choices. Since Google’s business model rests on targeted advertising, they care primarily about serving companies’ interests rather than yours. That’s why they appear to manipulate search results and display information designed to influence you without your knowledge. That includes being able to create an email address without using a phone number. Enter an optional email address or phone number that you can use to recover your account if you ever forget or lose your password. If you choose Email, you must provide a non-Proton Mail account to receive a code.
What Is The Dark Web? How To Access It Safely?
Nonetheless, takedowns usually result in valuable threat-intelligence grabs that benefit the cybersecurity community and intelligence that cannot be obtained anywhere else. “The threat intelligence gained from takedowns contributes to other law enforcement investigations. But the pace at which takedowns occur, the evolution of the threat actors will continue to outpace law enforcement capabilities,” Kroll says. Cryptocurrencies weren’t so popular among the general public until recently. However, dark web users have relied on Bitcoin transactions for over a decade, as they allow people to make payments while staying completely anonymous. And Hidden Wallet is one of your best options if you’re looking for a Bitcoin wallet for use on the dark web.
The Dark Lair aims to balance breadth of coverage with usability, making it a solid choice for newcomers and experienced users alike. While the Tor Browser provides strong anonymity, using a VPN (Virtual Private Network) alongside it adds an extra layer of security and privacy. A VPN encrypts your internet traffic before it enters the Tor network, hiding your Tor usage from your internet service provider and shielding your IP address from the first Tor relay. This setup can help prevent network-level surveillance and reduce risks in environments where Tor use might be flagged or restricted. Choose a trustworthy VPN service that has a strict no-logs policy and supports connection without DNS leaks. Avoid free VPNs as they often lack adequate security or monetize user data.
Protecting Yourself On The Dark Web
The dark web isn’t called “dark” because it’s inherently bad; it’s called dark because it provides privacy (that can be used for good and ill). The dark web is much like the regular World Wide Web we’re all familiar with, except that the dark web provides much greater privacy. Use Norton VPN to encrypt the data you send and receive and surf more anonymously. Even completing a transaction is no guarantee that the goods will arrive. Many need to cross international borders, and customs officials are cracking down on suspicious packages.
Experience The World’s Most Advanced Cybersecurity Platform
However, note that the site only uses non-sensitive and public data for the metrics. The Tor Metrics is a good place to get more information about the Tor project. It collects data from the public Tor network and archives historical data of the Tor ecosystem.
- That said, you still might get malicious links in your search results, so you still need to proceed with caution with any page DuckDuckGo takes you to.
- For instance, if you choose a topic (e.g. food), G-Feud will give you a string such as “can I eat…?
- However, there’s a chance you may run into illegal activity on all but the best onion sites.
- It was initially created to provide additional security and eliminate cryptocurrency theft.
- You can also take a look at the blogs & essays section if you want to find some nifty coding resources.
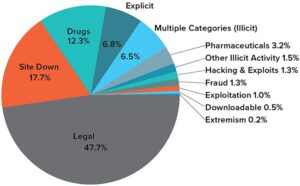
Risks And Dangers Of The Dark Web
A substantial portion of users turn to the Tor browser for its promise of anonymity, while others seek the additional security it provides. Curiosity about what the dark web has to offer also drives about one-third of its users. Additionally, hidden wiki websites function as directories of categorized .onion links, providing common entry points for users delving into the hidden internet. If one tries to visit the dark web with a regular browser, there will be no web pages to visit. Since the dark web is hidden from the surface web, these dark web search engines allow users to explore the concealed part of the Internet.
VPN‑Only Browsing
As stated above, we don’t condone any activity—on the dark net or otherwise—that is forbidden by law. Activists, whistle blowers, and journalists also use the dark web to communicate securely with sources and news organizations. Wasabi Wallet is a Bitcoin wallet that not only hides all your data in the Tor network but also allows you to “join” your transactions with others to increase your anonymity. AI-as-a-service (AIaaS) platforms offer many of these capabilities that lower the barriers for cybercriminals to carry out these attacks.

The tip of the iceberg floating above the surface is the portion of the internet we can access through normal means — i.e. browsers and search engines. For example we have a ‘staging’ version of this very website that is blocked from being indexed by search engines, so we can check stories before we set them live. Thus for every page publicly available on Tech Advisor (and there are literally millions), there is another on the Deep Web.
How Do I Use A VPN With Tor?
Drugs, weapons, and stolen IP and data are all hot businesses on the dark web, with terabytes of information on offer. Traders cash in on stolen credit card data dumps, initial access points to vulnerable systems, credentials, and intellectual property belonging to companies compromised during cyberattacks. You could consider the clear or surface web the “top” and visible layer of the internet, easily accessible using a browser such as Safari, Chrome, Edge, or Firefox.

Is The Dark Web Illegal?
Tor Browser prevents someone watching your connection from knowing what websites you visit. All anyone monitoring your browsing habits can see is that you’re using Tor. The dark web is content that exists on dark nets, which require specialized software (like the Tor Browser), configurations and authorization to access.
Belarus requires VPN providers to register with the government, and unregistered use can trigger administrative fines. Kazakhstan criminalizes “distribution of information facilitating drug trafficking,” which prosecutors have applied to forum posts linking to .onion addresses. The deep web, also known as the “invisible web”, is often incorrectly conflated with the dark web. Indeed, Proton offers an onion dark web version of our website so that people in some of the most repressive parts of the world can access our services. In many places, including the U.S., the UK, and the EU, accessing the dark web is legal for legitimate purposes. However, many sites on the dark web host illegal content or activities, and engaging with those can lead to serious legal consequences.
If you loved Elephind and want an alternative, you’ll be happy to know that all of its library is still accessible via Veridian’s website. Veridian aims to provide a single portal to all the historical newspapers of the world. It’s a fantastic resource for researchers—especially family historians, genealogists, and students. While no approach is foolproof, a thoughtful, criteria-driven strategy ensures a more secure and beneficial experience on the dark web.

Social Media
Unlike Ahmia and Haystak, however, DuckDuckGo doesn’t search .onion sites. Use it to search the normal internet from the privacy of your Tor Browser. Haystak also offers a premium version that allows advanced search, access to historical content, and email alerts. Your real information could be exposed at these nodes, allowing third parties to intercept your dark web activity.
This double encryption also protects against compromised Tor entry nodes that could potentially monitor your activity. Both DuckDuckGo and Ahmia are safe choices for finding Tor Browser links without being tracked. Any onion websites you visit from these search engines is another story. However, there’s a chance you may run into illegal activity on all but the best onion sites. Most internet users want to use the dark web safely, but it’s still important to be careful when using any onion browser.
All messages are encrypted, and the company does not log your IP address. It lets anyone send and receive email anonymously via webmail or with an email client. Popular news publications like The Washington Post, The Guardian, TechCrunch, and more have set up their own SecureDrop URLs so whistleblowers can contact them effortlessly. SecureDrop claims that all the messages you send and receive are encrypted in transit to prevent third parties from intercepting them. You can access Facebook via the dark web by using the official Facebook .onion mirror.