With a database comprising data from over 40 marketplaces, 23,000 vendors, and featuring more than 1.3 million reviews, Recon offers an unparalleled depth of information. Its clean, simple interface ensures ease of navigation for a diverse user base including buyers, vendors, and researchers. Primarily favored by individuals interested in procuring illicit goods and services from Dark web markets, Candle provides a straightforward and minimalistic user interface. It presents users with the top ten most relevant search results, akin to its mainstream counterpart, Google. However, it’s worth noting that Candle struggles to interpret certain characters like parentheses or quotation marks, posing a limitation to its functionality. Its user-friendly interface makes navigation a breeze, offering uncensored and unrestricted web search results.
Choose A Dark Web Search Engine
OnionLand and NotEvil, with their mobile-friendly designs, are poised to lead this trend. Before the dark web, early internet anonymity efforts emerged with systems like Freenet (2000), a peer-to-peer platform for censorship-resistant publishing. Each section includes a robust overview, expanded Key Features, Use Cases, Limitations, Real-World Examples, and Personal Take, plus the web address for each engine.
Can I Find Legitimate Resources On The Dark Web?
Haystak doesn’t filter harmful content, leaving users to navigate risks themselves, making it better suited for experienced researchers or journalists with robust security setups. I always cross-check its listings with Torlinks or r/onions to avoid traps, and I’ve learned to spot clones by checking link patterns. For beginners, it’s a gentle introduction to the dark web, but for pros, it’s a launchpad to pair with proper dark web search engines. Its .onion link is bookmarked, but I treat it as a starting point, not a destination. In reality, the deep web encompasses all parts of the internet that standard search engines like Google can’t access.
Navigating Ransomware Attacks While Proactively Managing Cyber Risks
ThreatMon offers comprehensive cyber security solutions in line with company needs. Since 2018, it has actively aimed to protect companies against external threats. As you might expect, Bitcoin is the top cryptocurrency being used on the Dark Web. Chainalysis says that $790 million worth of cryptocurrencies were used to shop in darknet markets during 2019. While some studies have claimed that illegal Bitcoin activity is as high as 44%. Simply accessing the dark web and using the Tor browser may already raise government suspicion.
They complement established ones like NotEvil, offering fresh features for niche research. Ahmia suits cautious users needing clean, multilingual searches, while Torch is better for power users tolerant of outdated UIs and manual verification, but it poses higher risks of scams. It’s beginner-friendly with simple keyword searches and no registration required, making it easier to explore privacy tools or forums without overwhelming clutter. By 2029, engines may support DID-based access to gated .onion communities, streamlining research while preserving privacy.
Subscribe To The Blog Newsletter

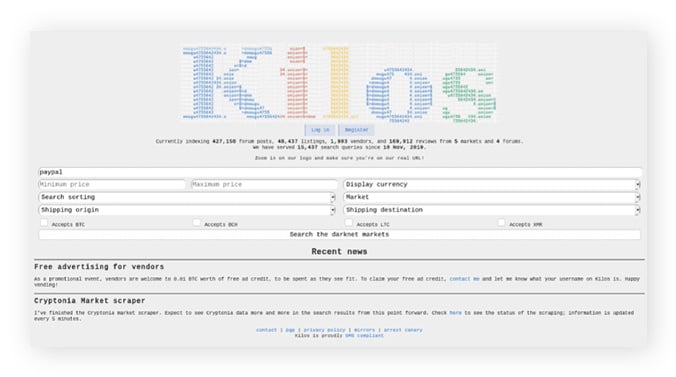
With an impressive database boasting over 122,811 listings and 7,782 vendors, Kilos provides users with a wealth of options to explore. When searching the darknet, OSE’s informative search page proves invaluable. It not only displays websites but also indicates whether the URL is currently online or offline—a crucial feature given the transient nature of .onion domains. Additionally, OSE provides the “last update” date for each URL, enhancing user transparency and trust. To access Recon Dark Web Search Engine, users must utilize the Tor browser, specifically designed to connect to hidden websites on the Dark Web.
What’s The Difference Between Torch And Ahmia?
Following these precautions and being mindful of ethical use cases will allow you to navigate the dark web more safely. Always monitor potential threats and stay aware of the risks involved. Therefore, you should understand the legal risks of accessing the dark web before you venture into this murky world. Accidentally downloading or viewing illegal materials may result in severe legal consequences.
- You will never know when you stumble upon illegal materials, inadvertently download malicious software, or expose yourself to identity theft.
- Keeper has millions of consumer customers and the business solution protects thousands of organizations worldwide.
- Some users also share links on encrypted apps like Telegram or Keybase that you can check.
- Use community-trusted directories, forums, and check reputation scores or comments on Reddit/darknet forums.
- The Hidden Wiki is a popular directory listing useful .onion websites and dark web search engines.
To access these resources, you need to log in with a username and password using a traditional browser like Chrome or Safari. The dark web often connotes illicit activities like illegal drug sales and hacking. However, it also supports legitimate uses like protecting free speech and accessing information in censored regions. Stolen and leaked data is bought and sold in parts of the dark web, as is malware as a service that can be used to attack your networks. By searching and monitoring the dark web, you can catch threats and stolen data before your assets are exploited by threat actors.
- You’ve no doubt heard talk of the “dark web” as a hotbed of criminal activity — and it is.
- And the search box can’t read certain characters like parentheses or quotation marks, which can be limiting.
- Not Evil is a dark web search engine specifically designed for “.onion” sites.
- But human trafficking, illegal pornography featuring underaged victims, money laundering, and assassinations are also examples of the darkest corners on the dark web.
- To navigate Haystack more easily and use its different features, you need to pay a certain amount.
- Are you curious about the mysterious world of the dark web but feeling a bit overwhelmed?
Therefore, you should avoid downloading files from the dark web, as seemingly innocent files may contain malicious software. Suppose you share your name, social security number, or any other personally identifiable information on any dark website. In that case, there is a high chance that your data will become accessible to cybercriminals. Then, they can use your data to impersonate you and run social engineering attacks to target your loved ones. You might visit the dark web seeking anonymity or unique services, but this anonymity also attracts scammers. You may encounter fake marketplaces promising illicit goods or services but delivering nothing after payment.

Disable Java And ActiveX In Your Network Settings
Furthermore, .onion websites are constantly changing locations, disappearing, or popping up in new forms, adding to the challenge. Because of this, there’s no single dark web search engine that covers everything comprehensively. Instead, users rely on a handful of specialized search tools, each indexing a different slice of the dark web landscape. LibreY is a secure dark web search engine that prioritizes privacy by operating without JavaScript, a commonly used programming language that can be used to track web activity. If one tries to visit the dark web with a regular browser, there will be no web pages to visit.
How To Access The Dark Web: Step-by-Step Tutorial (and A Few Words Of Caution)
DuckDuckGo, known for its privacy-focused approach on the surface web, also has a presence on the dark web. DuckDuckGo does not track your search history or collect personal data, making it a strong privacy-preserving option for searching both the surface and dark web. “I’ve been using Forest VPN while exploring the dark web for research. I feel secure knowing my data is protected,” shares Emily, a cybersecurity enthusiast. Discover how to use a darkweb search engine safely while enhancing your online privacy and security. Known for its broad index, Haystak offers both free and premium versions.
BBC News (and Other Leading News Sites)
Reddit is actually available on the dark web now, so there’s no need to rely on third-party tools to access it via Tor. Just bear in mind that the addition of anonymity to a platform like Reddit causes people to behave without a filter. We also urge you to remember that there are various versions of the Hidden Wiki circulating on the dark web. The original (linked below) is still considered the most reliable, so try to avoid counterfeit versions. You can use this community-edited link database to find everything from anonymous chat rooms, to Dark Web social networks, and blogs about various interesting subjects. The Hidden Wiki is one of the easiest ways to find useful resources and websites on the Dark Web.
Practical Guidelines To Manage Risks:
It provides unrestricted and uncensored search results, allowing access to a wide range of hidden content. This isolates any potential malware and prevents cross-contamination with your personal data. Using Tails OS can further security, as all your data is reset every time you close the device. A reliable VPN encrypts your traffic before it enters the Tor network, preventing surveillance from your ISP or malicious actors. During my tests, ExpressVPN’s military-grade encryption and verified no-logs policy provided consistent protection against tracking and monitoring.