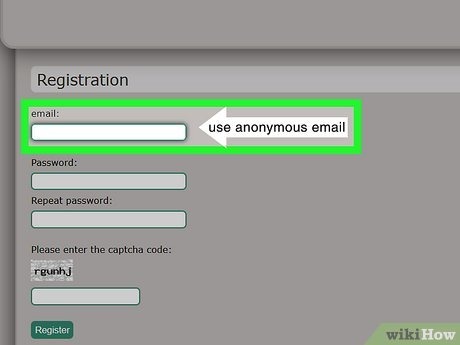
When accessing the Dark Web, it’s crucial to protect your personal information. Avoid using your real name, email address, or any personally identifiable information. Create anonymous usernames and use secure passwords for any accounts you create. Onion websites on the Dark Web have addresses ending in .onion instead of the usual .com or .org. They are designed to be accessed exclusively through the Tor Browser.
However, it’s important to take some additional steps to ensure your safety. JavaScript is a common vector for security exploits, and disabling it can help protect you from potential threats. Additionally, you should never provide personal information or use your regular email address while on the Dark Web.
Its lack of robust filtering means users encounter spam, scams, and illegal content, making it better suited for experienced navigators comfortable with manual verification. These tools are the dark web’s rogue librarians, mapping a realm where traditional rules don’t apply. They lack the scale or polish of surface web engines but are critical for exploring what’s deliberately hidden. Implementing effective dark-web monitoring is crucial for proactively detecting and mitigating data breaches.
So, even though it does exist on the internet, Google doesn’t index any of these pages or content. Google considers the majority of the content on the entire web highly irrelevant and useless to its users. That’s why such a large percentage (as much as 94%) of the entire web is not returned in Google Search. KEY TAKEAWAYS Tor is one of the most popular private browsers in the industry.
What Should I Avoid On The Dark Web?
If you need to create accounts on dark web services, use a burner email and never reuse usernames or passwords from your real life. If you must purchase anything on the dark web — which I don’t recommend — you should always pay in cryptocurrencies. Remember that good judgment, ongoing education, and constant vigilance are your most powerful tools for maintaining a safe and private Dark Web experience.
Step 1: Gather The Required Tools
It’s up to you whether you wish to use your own name or an alternate name if the package is being delivered to your home address. Tick the box to confirm that you don’t reside in Australia and agree to the terms of service. If you already own bitcoin, or have obtained some using one of the methods described above, you can skip this section. Otherwise, here’s how to purchase your first BTC on Localcryptos.com.

How To Get On The Dark Web In 2025: A Step-by-Step Guide
By keeping an eye on these alternative platforms and trends, you gain a deeper understanding of how privacy, anonymity, and underground markets adapt to new technologies and challenges. As digital ecosystems morph, staying informed and agile will help you make the most of evolving privacy tools—or avoid stepping into ever-more complex traps. This means that the identities and locations of darknet users are hidden from public view and remain anonymous, even when interacting with other users or engaging in any online activity. However, this does not provide any extra security for your device or information. A VPN allows a user to encrypt all internet traffic traveling to and from his or her device and route it through a server in a location of that user’s choosing. A VPN, in combination with Tor, further enhances the user’s security and anonymity.
How To Access The Dark Web Safely: Step-By-Step
The “Hidden Wiki” (which can be accessed in a normal browser) offers a large collection of dark web links, but be careful, as many of those links are to dangerous websites. Later on, the underlying Tor code was released into the wild under a free license, leading to the formation of the Tor Project. In 2008, the first Tor Browser was released, making it easier for any internet users to access the dark web. In 2002 the dark web began to grow significantly when researchers backed by the U.S.

Anonymity Is In Your Hands
Best YouTube TV VPN – Learn how to bypass or hack YouTube TV location restrictions outside the US easily. Legal Repercussions – Law enforcement devotes immense resources to tracking certain dark web sites and transactions. However, many listed sites could be malicious, so proceed with extreme caution especially before entering any credentials.
How To Access The Dark Web On Android And IOS
- It’s extremely rare and only useful in very specific cases, like if your VPN is only accessible through Tor.
- Doing so can tie your activity back to you, destroying your anonymity.
- It includes media and archives which cannot be crawled and indexed with current search engine technology.
- Exercise caution when clicking on links or downloading files from the Dark Web.
- Tails is a mere 1.3 GB download, so on most connections it will download quickly.
In this comprehensive, SEO-friendly guide, we’ll walk you through how to access the Dark Web step by step, what tools to use, how to stay safe, and what precautions to take. On the other hand, the VPN provider may notice you are on Tor and opt to store your metadata logs, but they cannot view the content of your encrypted Tor connection. Therefore, you should select a VPN service that does not save traffic logs containing metadata like your IP address. If you are a journalist or whistleblower and want to access the dark net for legal purposes, this guide is for you. Successfully navigating this hidden world requires preparation, vigilance, and a thorough understanding of both the technical and ethical challenges at play.
Thus, you will be able to explore the expanse of this depth without suffering from its heights of risk. A Virtual Private Network, or VPN, simply lets you access the dark web. It encrypts your internet traffic and hides your IP address, which makes it extremely difficult for anyone, even your ISP or evil actors, to track what you are doing. If you want to improve your security further, you could also use a VPN at the same time as Tor. For the most security-conscious, you can even install the Tails operating system on a flash drive and run Tor from that.

Which Is The Best Laptop For Cyber Security Course?
With your VPN up and running and all of your other apps closed down, you’re finally on the brink of actually accessing the dark web. To access the surface web or the deep web, all you need is a standard internet browser like Google Chrome or Safari. For the dark web, though, you need an entirely different entry point known as an overlay network. Because VPNs offer users anonymity and mask their actual location, they’re also effective tools for accessing geo-locked services.
Torch: The Sprawling Veteran Of Dark Web Search
It would be problematic if someone could open your private email chains through a simple Google search. An easy way to think about this is if you need a username and password to access it, it’s a part of the deep web. No matter what you do online, there’s always at least some risk of being tracked — especially on the dark web.



