
It provides an .onion URL and an interface for you to manage your Tor site easily. It also boasts that no personal information is required to use the service, and payment can be made with cryptocurrency. Keybase is an exciting identity service that aims to make it easy for you to link the presence of your online identities together in a cryptographic way.

Hidden Answers
If you make use of a password manager, then it may come with a feature that monitors the dark web for mentions of your email address and password, or any other personal details. It’s something built into the password management services offered by Apple and Google as well, so you don’t need to trawl through data leaks manually yourself. Individual sites on the dark web look much like they do on the regular web, though a lot of them are a bit more rough around the edges. (Presentation and polish isn’t quite so important on this part of the internet.) Click on any website link, and it’ll appear on screen, with its address at the top. Open up Tor, and you won’t suddenly see the dark web staring back at you. Not only do you need a dark web browser, you need a dark web search engine too.
Absolutely no one knows who’s surfing on the dark web, who is selling, who is buying or anything like that – as long as you take the correct safety and online privacy precautions. For example, the deep web is often a platform used by political activists who own a blog. But it also contains other news and religious sites, private discussion forums, and medical records. So, sites that contain a domain extension like .com, .org, .net, .biz, .info, etc. can be found on the surface web.

Method II – VPN Over Tor
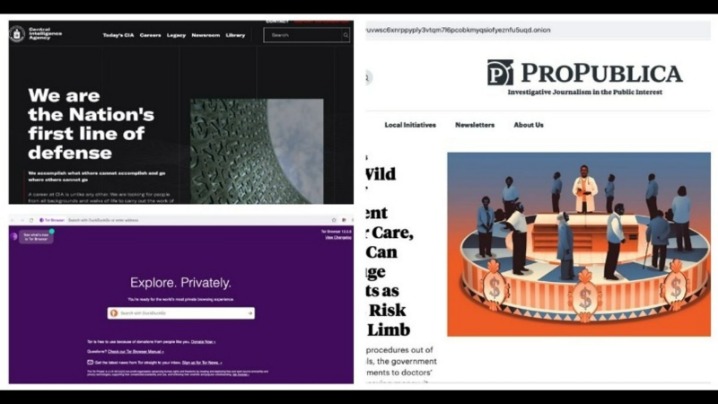
The best Tor sites are under constant threat of closure, including Tor directories like the Hidden Wiki, so having a backup in case one goes down is handy. ProPublica is a non-profit, Pulitzer Prize-winning news outlet that focuses on abuses of power and issues of public trust. ProPublica’s investigative journalism can upset powerful interests, so the outlet joined the dark web to help their journalists and readers access their content anonymously. Being on the dark web also lets whistleblowers send material to ProPublica without fear of reprisal. ZLibrary hosts free file-sharing access to academic texts, scholarly articles, and general-interest books. It often hosts copyrighted materials without permission, violating many countries’ copyright laws.
The Mail Plus plan adds up to 15 GB of storage, unlimited messages, and 10 email addresses, plus advanced email settings (like automatic forwarding). You can also get Proton Unlimited and Proton Duo plans that add even more extras. The developer, Konstantinos Papadakis, indicated that the app’s privacy practices may include handling of data as described below. In today’s digital era, where information is constantly on the move across all digital platforms, an… However, you can check out this guide for the best ad blockers to avoid annoying ads.
Can I Be Traced, Tracked, Or Hacked If I Access The Dark Web?
The VPN will protect your traffic when you connect with military-grade AES 256-bit encryption. This is high-level protection; no one can intercept your data or activities. Your online activity and communications remain private and secret on the dark web. Because of this, some people use it to get around government restrictions, while others use it for illegal activities like smuggling drugs and weapons. All in all, it is not illegal to access the dark web, but it can create issues for you.
Does The CIA Have An Onion Site?
Brave Browser integrates Tor technology directly into its platform, offering users an accessible, user-friendly gateway to the dark web. Users can easily open Tor-enabled private tabs alongside their regular browsing sessions, making it ideal for seamless and secure browsing experiences. The dark web is neither entirely a haven for illicit activities nor a utopian space of limitless freedom. Instead, it represents a complex ecosystem where anonymity can serve both noble causes—such as protecting free speech and enabling investigative journalism—and darker ends.
Protecting your digital identity is crucial when navigating the dark web. Password managers and anonymous email services prevent unauthorized access and ensure private communications. While no single tactic is foolproof, a layered approach—combining technical, operational, and psychological defenses—greatly improves your safety and confidence when navigating the dark web. Law enforcement agencies keep an ear to the ground on the dark web looking for stolen data from recent security breaches that might lead to a trail to the perpetrators. Many mainstream media organizations monitor whistleblower sites looking for news.
- Torch is funded primarily through advertising—purchased in BTC, of course—which is why you’ll find the front page blanketed with old-school banner ads of dubious origins.
- The US government initially created Tor as a tool for different military organizations to exchange messages and information anonymously.
- Additionally, hidden wiki websites function as directories of categorized .onion links, providing common entry points for users delving into the hidden internet.
- Unlike the surface web, which we access daily through browsers like Chrome and Firefox, the dark web requires specific browsers to maintain user anonymity and ensure secure access.
A dark web browser is a specialized tool that enables users to access the “dark web”—an encrypted, private network that hosts websites not indexed by mainstream search engines. Unlike the surface web, which we access daily through browsers like Chrome and Firefox, the dark web requires specific browsers to maintain user anonymity and ensure secure access. To find what you’re looking for, you may need to try multiple search engines or visit directories of trusted .onion links. If you need an idea of where to start, check out our list of the best dark web sites in 2025. Using a dark web search engine is a great step towards enjoying a more secure experience while shopping on the platform. Not all marketplaces you want to visit can be accessed through regular search engines.
The Camouflage Mode is intended for people living in countries with heavy internet censorship, like China. It will make your VPN activities seem like normal traffic, so you can use an uncensored internet. However, this feature is only available on iOS, Android, and Windows. A top-of-the-line VPN network that ensures maximum security while accessing dark sites online.
Is It Illegal To Visit Websites On The Dark Web?
Facebook’s onion version lets people access Facebook in countries where access to the social network is otherwise restricted. Facebook’s dark web website helps people around the world connect, communicate, and organize. So Facebook’s onion portal is a valuable tool for people living under repressive regimes. These URLs are usually very long, consisting of a random jumble of letters and numbers. Though you likely won’t remember the addresses of onion websites, you can find these URLs on various websites on the internet. Hackers there might have tricks up their sleeves to track your location through GPS or WiFi, and they could potentially access other sensitive information on your device.
Is It Illegal To Access The Dark Web?
In general, the rules for accessing the deep web and the dark web safely are very similar to the best practices for accessing the surface web. Your safety on the dark web depends more on cautious browsing habits than any single security tool. While a VPN adds valuable protection, being selective about which sites you visit and never sharing personal information are equally important.
Ensure your Tor browser is always up-to-date– automatic updates are enabled by default, but if turned off, you should manually update it regularly. For example, state-level actors can execute traffic correlation attacks, wherein they monitor both incoming traffic at the entry nodes and outgoing traffic at the exit nodes. By observing these patterns, they can link a Tor user’s request to a server and reveal their intended destination. Tor traffic is decrypted at the exit node, which opens a vulnerability for malicious actors to inject malware or intercept traffic.
Boost Your Privacy When Browsing The Web With A VPN
Yes, but you need to be cautious because there are many malicious sites on the dark web. The best way to do that is to get the link from legitimate sources, like The Hidden Wiki. What’s more, you should always use a VPN (like ExpressVPN) with Tor to protect yourself from IP leaks. I also recommend using an antivirus (like Norton 360) to protect your device from malware infections. In addition to these tools, you need to exercise extreme caution when browsing on the dark web because there are tons of phishing and malicious sites on there. Only use .onion links that come from legitimate sources like The Hidden Wiki.
One way to stay safe is to use a VPN while accessing the dark web, so be sure to check out my article on the best VPNs for the dark web. The dark web (often referred to as the “darknet,” “black web” or “black net”) is a small section of the deep web that is hidden and kept inaccessible to regular internet users on purpose. While there are numerous VPN services that work well with Tor, I’ve found that NordVPN offers the best protection and compatibility, and keeps your personal information safe. This is why I strongly suggest using a Virtual Private Network to protect and enhance all of your online activities.



