
All ISO publications and materials are protected by copyright and are subject to the user’s acceptance of ISO’s conditions of copyright. Any use, including reproduction requires our written permission. By integrating top-grade security into their operations, organizations can not only reduce their exposure to cyber threats but also reinforce trust in an increasingly data-driven world. In a world where privacy is a luxury, Archetyp Market offers you the chance to keep your transactions discreet. A curated collection of darknet resources for educational purposes, offering insights into darknet frameworks, tools, and security practices.

STYX Market
Instead of simply routing traffic, Freenet stores encrypted chunks of data across nodes. The Dark Net section, on the other hand, details how to use the Tor browser to access dark web links (or onion links). This section focuses on the positive side of the dark web, which provides activists and journalists with the necessary online anonymity to carry out their advocacy without interference. Besides telling the stories of dark web victims, the book explores the criminal activities that take place on the dark web, such as scams, identity theft, drug trafficking, child porn, and more. It also explores the darker side of the dark web that encourages suicide, racism, and eating disorders.
Table Of Contents
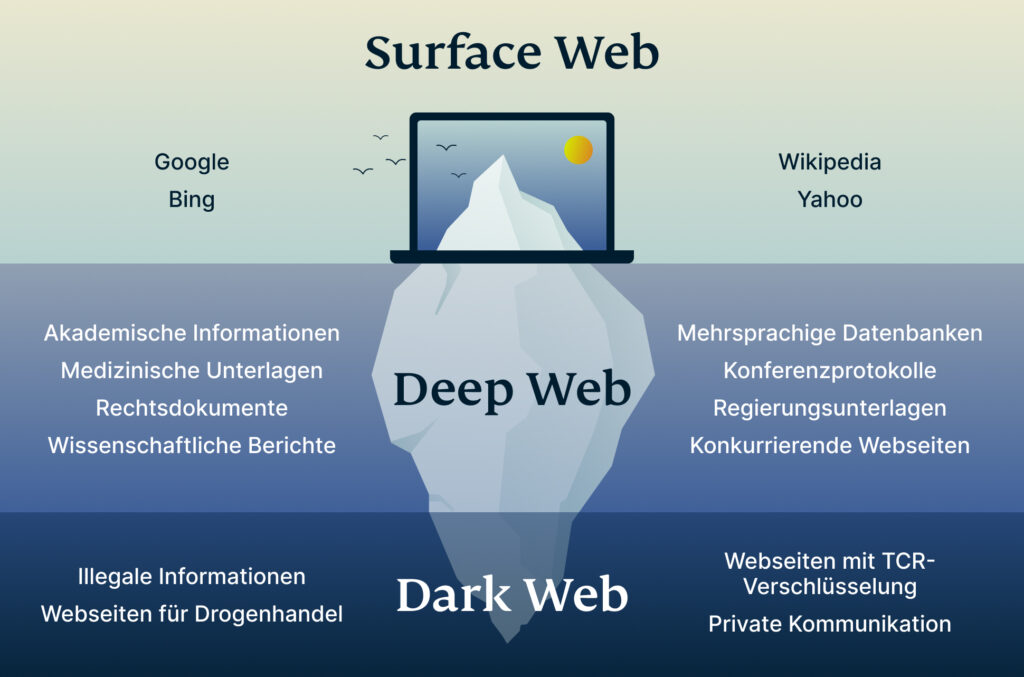
- The deep web is basically all the content that you can’t find using Google or Yahoo search.
- Additionally, MGM offers exclusive services like custom hacking solutions, malware programs, and sought-after data dumps, cementing its position as an innovator in the darknet marketplace.
- The Tor Project began experimenting with hybrid algorithms in 2024, and I2P is exploring lattice‑based schemes for secure routing.
- You’re only scratching the surface when you use the Internet for daily activities—reading news, managing finances, running businesses.
The dark web didn’t start as a haven for cybercriminals – it was actually developed for a very different purpose. Originally created by the US military to enable secure and anonymous communication, this hidden layer of the Internet has since evolved into a complex digital underground. The Dark Web EcosystemAs part of the dark web, Dream Market was accessible only through Tor, official onion link. The platform quickly became a major player in dark web commerce, drawing comparisons to earlier sites like Silk Road. See how our intelligent, autonomous cybersecurity platform harnesses the power of data and AI to protect your organization now and into the future. Darknets also serve as a platform for whistleblowers and privacy advocates.
Can I Access The Dark Web With The Tor Browser?
Freenet was originally intended to provide a way to anonymously interact online, providing ways to communicate, exchange information and files, and to otherwise communicate incognito. But human trafficking, illegal pornography featuring underaged victims, money laundering, and assassinations are also examples of the darkest corners on the dark web. Typically, any reference to the visible web will be to common websites with a familiar internet domain extension. Google considers the majority of the content on the entire web highly irrelevant and useless to its users. That’s why such a large percentage (as much as 94%) of the entire web is not returned in Google Search. It might sound weird that Google doesn’t index these pages, but it does carry some logical sense.
Explicit Content
NordVPN delivers a safe and private Internet connection, ensuring that your identity and internet usage are entirely anonymous. VPN provides another degree of protection and allows you to access Dark Web connections that may be blocked in your location. NordVPN is your best chance for safely accessing the Dark Web, thanks to customer controls and solid security. It is crucial to emphasize, however, that the Dark Web may be dangerous, and even with NordVPN, vigilance should be constant in order to avoid frauds and criminal activity.
More On Tor Onions
The area of the internet we access daily is known as the clear or surface web. In today’s digital era, where information is constantly on the move across all digital platforms, an… Following its popularity, the marketplace attracted GBI, IRS, and other government agencies’ attention, leading to Ross’ arrest in 2013 and later life imprisonment for his role in operating Silk Road. As a matter of fact, your data could be anywhere on the internet, meaning it could already be at the three internet levels (surface web, deep web, and dark web). With all this data, your ISP could create a very accurate profile of you and link it to your IP address.

Dark Web Chat/Social Networks
However, some Tor users do so to facilitate illegal online acts. In addition, NordVPN offers Onion over VPN (think Tor over VPN), which routes your internet traffic through one of its servers, passes it through the Onion network, and then sends it to the internet. This means you can use your favorite browser instead of the Tor Browser and still benefit from being routed through the Onion Network.
The Tor Project, a research-education nonprofit, was founded in December 2006 to maintain the software. Bear in mind too, that your internet provider will be able to see you connecting to Tor nodes, even if it doesn’t know exactly what you’re doing. Many people install a VPN as well, but then you’re putting your trust in an additional third party to not track your activities or report them to anyone else. Disable JavaScript in Tor until you trust the site you’re visiting.
As we’ve pointed out throughout this article, the dark web is pretty much a jungle where anything goes. There’s no one regulating anyone, which allows bad-faith actors to do whatever they want, including targeting innocent people. If you want to navigate this space safely, you need to invest in a dark web book with a helpful guide.

Tor is a network of volunteer relays through which the user’s internet connection is routed. The connection is encrypted, and all the traffic bounces between relays worldwide, making the user anonymous. The looming threat of quantum computing has sparked adoption of post‑quantum cryptography in anonymity networks. The Tor Project began experimenting with hybrid algorithms in 2024, and I2P is exploring lattice‑based schemes for secure routing. These safeguards aim to future‑proof traffic from potential decryption by quantum‑enabled adversaries.
Reasons for this could be to show a commitment to privacy or allow people to pass them information anonymously. The Guardian newspaper has a SecureDrop facility on Tor – as does the CIA – which uses it for virtual walk-ins for anyone wanting to confidentially pass them information. This is where things might get just a bit confusing, as the Dark Web is nearly synonymous with illegal activity. Indeed, the vast majority of activity taking place there is illegal. In attempting to access the Dark Web, there’s an invisible line that a person acknowledges they’re crossing – or maybe they don’t.
This is where cybercriminals go to buy and sell things like stolen credit card numbers, personally identifiable information (PII), and even SSH login details. One thing that distinguishes BidenCash on the dark web, however, is how it markets itself. Whether you want some pharmaceutical products (drugs) or digital items, you will probably find the products here, and that too at affordable prices.



